In Brief (TL;DR)
In summary, ATM security is a delicate balance between system protection and responsible user behavior.
Vulnerabilities exist, but countermeasures are effective if implemented correctly and if everyone, operators and users, does their part.
Awareness of risks and the adoption of best practices are the keys to using ATMs safely and protecting our savings.
The devil is in the details. 👇 Keep reading to discover the critical steps and practical tips to avoid mistakes.
Welcome to the digital age, where technology permeates every aspect of our daily lives. Among the most appreciated conveniences, ATMs stand out as faithful allies for withdrawing cash, checking balances, or topping up accounts at any time. But behind the reassuring facade of these machines lie gray areas, weak points that, if not understood and managed correctly, can turn into serious threats to our financial security.
In this article by TuttoSemplice.com, we will dive into the beating heart of ATM security, analyzing vulnerabilities from both the system and user perspectives. Our goal is to provide you with a complete and in-depth guide, capable of revealing hidden risks and offering practical tools to protect your hard-earned savings.
Get ready to discover:
- The security flaws intrinsic to the ATM system, often invisible to the untrained eye.
- The risky behaviors of users that, unintentionally, throw the doors open to cybercriminals.
- The most effective defense techniques, for both ATM operators and customers, to navigate the world of ATMs with greater awareness and peace of mind.
Fear not, we won’t overwhelm you with incomprehensible technical jargon. Our style, in the tradition of TuttoSemplice.com, will be clear, direct, and accessible to everyone. We will use simple language, concrete examples, and practical advice to put into practice immediately.
Are you ready to protect your money and become a more aware and secure ATM user? Then continue reading and discover the ATM weaknesses that no one has ever told you about!

ATM System Weaknesses: When Technology Isn’t Enough
ATMs are complex systems, a true powerhouse of technology that includes hardware, software, and communication networks. Like any technological system, ATMs also present intrinsic vulnerabilities, weak points that can be exploited by malicious actors to compromise their security. In this chapter, we will analyze these security flaws in detail, focusing on the three main fronts: software, hardware, and network.
Obsolete Software and Missing Security Patches: An Invitation for Hackers
The software that powers ATMs is the true brain of the machine, the conductor coordinating all operations. Obsolete software, not updated with the latest security patches, becomes a privileged gateway for cybercriminals. Imagine a castle with solid walls, but with an old, rusty back door that is easy to force open: that is exactly what unupdated software represents.
Software vulnerabilities can be of various types, from programming bugs to configuration errors, up to hidden backdoors—actual secret passages left open, voluntarily or involuntarily, by the software creators. These vulnerabilities can be exploited to install malware on ATMs, intercept card data, manipulate transactions, or even take complete control of the machine, turning it into a free cash dispenser for criminals.
A concrete example? The Ploutus malware, one of the most notorious in the ATM world, exploits the very vulnerabilities of the Windows operating system, often present in ATMs, to empty cash dispensers. These attacks, unfortunately, are not science fiction, but documented reality, as demonstrated by numerous reports from cybersecurity companies and news articles that periodically report cases of hacked ATMs around the world.
Keeping ATM software updated is therefore fundamental, a true priority for ATM network operators. The timely installation of security patches released by software manufacturers is a crucial step to close the gaps and protect ATMs from cyberattacks. But, as we shall see, software is not the only front to focus on.
Vulnerable Hardware: When Security is Physical
ATM security is not just a matter of code and algorithms, but also of physical protection. The ATM hardware, the physical structure of the machine, represents another potentially exploitable weak point. An ATM located in an isolated, poorly lit, or inadequately protected place becomes an easy target for physical attacks of various kinds.
Among the most common hardware vulnerabilities, we find:
- Tampering with the shutter/slot: Criminals can force the ATM shutter to access the cassette containing the cash. Techniques such as crowbarring (using a lever) or explosives (though rarer and riskier) can be used for this purpose.
- Installation of skimming devices: Skimming, as we will see in detail in the next chapter, is a technique aimed at stealing user card data. To implement skimming, criminals install hardware devices (skimmers) on the card insertion slot or the ATM keypad. These devices, often difficult to spot with the naked eye, record the magnetic stripe data or the chip of the card, allowing criminals to clone cards and empty the victims’ bank accounts.
- Theft of the entire ATM: In some cases, criminals do not limit themselves to tampering with the ATM but steal it completely, loading it onto a van or truck. This technique, bolder and more complex, requires certain organization and means, but allows criminals to take away the entire loot, both the cash contained in the ATM and, potentially, the data stored within it.
To protect ATM hardware, it is fundamental to adopt adequate physical security measures. These measures include:
- Strategic positioning: Installing ATMs in crowded, well-lit, and video-monitored places, reducing opportunities for physical attacks.
- Alarm systems: Equipping ATMs with motion sensors, acoustic alarms, and video surveillance systems connected to security operations centers, capable of raising the alarm in case of tampering or attempted theft.
- Armoring and structural reinforcement: Using resistant materials for the construction of ATMs, such as armored steel, and reinforcing the structure of the shutter and the cassette, making physical access to internal components and cash more difficult.
Physical security and logical security (software) must go hand in hand, like two sides of the same coin. Neglecting one of the two aspects means exposing the entire ATM system to concrete risks.
Insecure Communication Networks: The Risk of Interception
ATMs are not isolated islands; they are connected to communication networks that allow them to interact with banks, authorize transactions, and transmit data. These networks, if not adequately protected, can become another exploitable weak point for intercepting communications and stealing sensitive information.
ATM communication networks can be of various types, from traditional telephone lines to dedicated networks, up to internet networks. Each type of network presents specific vulnerabilities. For example, telephone lines can be physically intercepted, while internet networks can be attacked via cyberattacks such as man-in-the-middle, where an attacker positions themselves between the ATM and the bank, intercepting and modifying data in transit.
Another risk related to communication networks is the use of insecure communication protocols or weak encryption. If the data transmitted between the ATM and the bank is not adequately encrypted, an attacker who manages to intercept the communication can read the data in plain text, obtaining sensitive information such as card numbers, PINs, and transaction details.
To protect ATM communication networks, it is essential to adopt secure communication protocols and robust encryption. The use of Virtual Private Networks (VPNs) can add an extra layer of security, encrypting all network traffic and protecting it from interception. Furthermore, it is important to constantly monitor networks to identify any suspicious activity or intrusions and respond promptly to any security incidents.
In summary, the weak points of the ATM system are manifold and concern software, hardware, and communication networks. Only a holistic approach to security, which takes all these aspects into account, can guarantee effective protection of ATMs and customer funds. But, as anticipated, ATM security does not depend only on the system, but also on user behavior. In the next chapter, we will analyze the weak points related to the user and see how we too, in our own small way, can do our part to protect ourselves from scams and thefts at ATMs.
User Weaknesses: When We Are the Risk
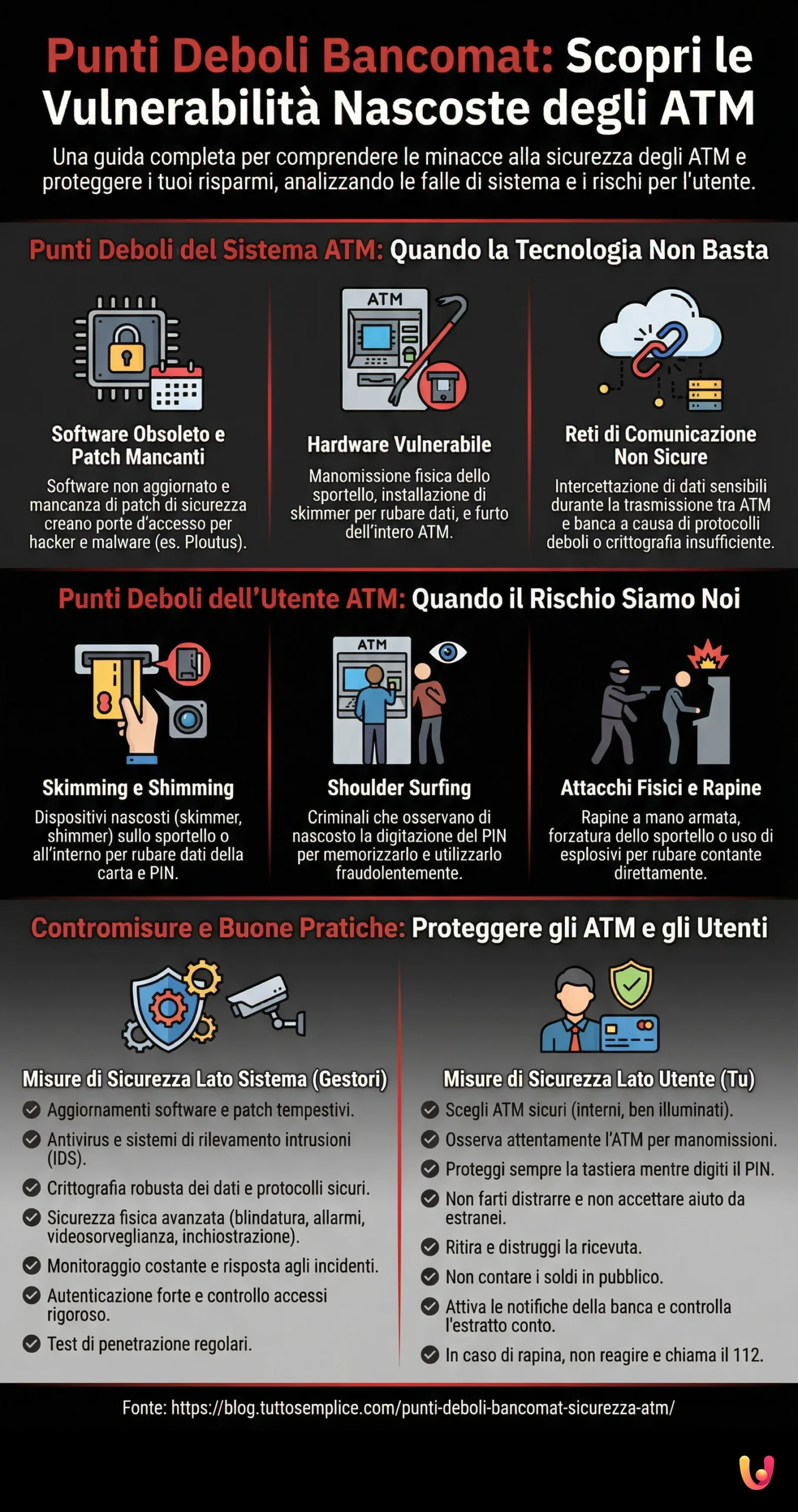
Even the user, unfortunately, can represent a weak point in the ATM security chain. Careless behaviors, distractions, or simple naivety can throw the doors open to criminals, making us easy victims of scams and thefts. In this chapter, we will analyze the main weak points related to the user, focusing on three threats in particular: skimming and shimming, shoulder surfing, and physical attacks and robberies.
Skimming and Shimming: The Invisible Trap in the Slot
Skimming and shimming are two devious techniques used by criminals to steal user card data at ATMs. Both techniques rely on the installation of hardware devices on the ATM, but they differ in the type of device used and the way data is stolen.
Skimming is the more traditional technique and consists of installing a skimmer, a thin and camouflaged device, on the card insertion slot. The skimmer reads the magnetic stripe of the card as it is inserted into the ATM, recording the data contained in the stripe. Simultaneously, criminals may install a hidden micro-camera to record the PIN typed by the user on the keypad. Once the card data and PIN are obtained, criminals can clone the card and withdraw cash or make online purchases at the victim’s expense.
Shimming, on the other hand, is a more recent and sophisticated technique that targets EMV chip cards, now the standard in Europe and many other countries. The shimmer is an even thinner device than the skimmer, inserted inside the slot, corresponding to the chip reader. The shimmer intercepts the chip data during the transaction, bypassing the protections that are theoretically more advanced in EMV cards. Also in this case, a micro-camera can be used to record the PIN.
How to defend against skimming and shimming? Prevention is the best weapon. Here are some practical tips:
- Observe the ATM carefully before using it. Check for signs of tampering on the card insertion slot, the keypad, or the surrounding area. If you notice anything suspicious, do not use the ATM and report the situation to the bank or the competent authorities.
- Check for additional devices superimposed on the slot or keypad. Try to wiggle the slot and keypad slightly: if they move or seem unstable, they may have been tampered with.
- Always protect the keypad with your hand while typing the PIN, preventing any micro-cameras from recording it. This simple precaution, often underestimated, can make the difference.
- If possible, use internal ATMs, located inside bank branches, which are generally safer than external ATMs exposed to greater risks.
- Activate SMS or email notification services from your bank to be alerted in real-time of every transaction made with your card. In case of suspicious transactions, you can block the card immediately and limit the damage.
- Regularly check your bank statement and card movements, promptly reporting any unauthorized transactions to the bank.
Skimming and shimming are real and concrete threats, but with a little attention and prevention, we can significantly reduce the risk of falling victim to these scams.
Shoulder Surfing: Prying Eyes Ready to Steal Your PIN
Shoulder surfing is a technique as simple as it is effective used by criminals to steal the PIN of users at ATMs. It simply consists of secretly observing the user while they type the PIN on the ATM keypad, memorizing it to then use it to withdraw cash or make fraudulent transactions with the stolen or cloned card.
Shoulder surfers can act in different ways:
- Loitering near the ATM, pretending to be waiting customers or distracted passersby, but actually watching the keypad closely while the user types the PIN.
- Using binoculars or hidden cameras to observe the keypad from a distance, perhaps from a car parked nearby or a building opposite the ATM.
- Collaborating with accomplices, one of whom distracts the victim while the other observes the PIN.
How to defend against shoulder surfing? Also in this case, prevention is fundamental. Here are some useful tips:
- Choose ATMs located in safe and frequented places, avoiding isolated or poorly lit ATMs where criminals can act undisturbed.
- Pay attention to the people around you while using the ATM. If you notice suspicious people watching you insistently, do not use the ATM and walk away.
- Always protect the keypad with your hand while typing the PIN, creating a physical barrier between the keypad and prying eyes. Use your other hand or your wallet to cover the keypad, making it impossible to view the PIN.
- Check that there are no mirrors or suspicious cameras pointed at the ATM keypad. Criminals can use mirrors or hidden micro-cameras to bypass protections and observe the PIN from different angles.
- If you feel watched or uncomfortable while using the ATM, stop the operation and walk away. Do not hesitate to trust your instincts.
Shoulder surfing is a simple but effective threat that exploits the distraction and lack of attention of users. With a little vigilance and precaution, we can protect our PIN and prevent thefts and scams.
Physical Attacks and Robberies: When the ATM Becomes Loot
Physical attacks and robberies at ATMs represent the most direct and violent threat to user safety. In these cases, criminals do not limit themselves to stealing card data or PINs, but aim directly at the cash contained in the ATM or in the user’s wallet.
Physical attacks can be of various types:
- Forcing the shutter: As already mentioned in the previous chapter, criminals can force the ATM shutter to access the cassette containing the cash. This technique can also be used while the user is using the ATM, interrupting the operation and threatening the user to hand over the withdrawn cash or the card.
- Explosions: In more extreme cases, criminals can use explosives to blow up the ATM and retrieve the cash. This technique is dangerous and destructive, but can be used in isolated places or during night hours.
- Armed robberies: Criminals can assault users while they are using the ATM, threatening them with weapons to hand over the withdrawn cash or the card. These robberies can occur both day and night, especially in isolated or less frequented places.
How to defend against physical attacks and robberies? In these cases, the reaction must be prompt and lucid. Here are some behavioral tips:
- Choose ATMs located in safe and frequented places, avoiding isolated or poorly lit ATMs, especially during night hours.
- Pay attention to the surrounding environment before using the ATM. If you notice suspicious people or anomalous situations, do not use the ATM and walk away.
- If you are approached by suspicious people while using the ATM, immediately stop the operation, retrieve the card (if possible), and walk away quickly.
- In case of robbery, do not react and do not resist. Your physical safety is the absolute priority. Hand over the cash or the card to the robbers and do not put your life at risk to defend material goods.
- After the robbery, immediately call 112 (European Emergency Number) and report the incident to the competent authorities, providing all useful details for the investigation.
- Immediately block the ATM card and contact your bank to report the robbery and prevent fraudulent use of your card.
Physical attacks and robberies at ATMs are rare events, but potentially dangerous. Prevention, awareness, and prompt reaction are the best weapons to protect our personal safety and limit damage in case of aggression.
Countermeasures and Best Practices: Protecting ATMs and Users

After analyzing the weak points of ATMs, both from the system and user perspectives, it is time to focus on solutions, countermeasures, and best practices to adopt to strengthen ATM security and protect users from threats. In this chapter, we will explore defense strategies on two fronts: system-side security measures, implemented by ATM operators, and user-side security measures, which we can adopt ourselves in our daily use of ATMs.
System-Side Security Measures: Technology and Vigilance to Protect ATMs
ATM network operators have the primary responsibility to ensure the security of the machines and customer funds. To do this, they must implement a series of system-side security measures, ranging from software and hardware protection to constant vigilance and timely response to incidents.
Among the most important system-side security measures, we find:
- Software updates and security patches: Keeping ATM software always updated is fundamental to correct vulnerabilities and protect machines from cyberattacks. The timely installation of security patches released by software manufacturers is a continuous and indispensable process.
- Antivirus and Intrusion Detection Systems (IDS): Equipping ATMs with antivirus software and intrusion detection systems allows for the identification and blocking of any malware or intrusion attempts into the system. These systems must be constantly updated and monitored to ensure their effectiveness.
- Data encryption: Encrypting sensitive data transmitted between the ATM and the bank, as well as data stored within the ATM, is essential to protect it from interception and unauthorized access. The use of robust encryption algorithms and secure communication protocols is an unavoidable best practice.
- Advanced physical security: Implementing advanced physical security measures, such as armoring, alarms, video surveillance, motion sensors, and banknote ink staining systems (which stain banknotes in case of tampering or theft), makes ATMs less attractive for physical attacks and facilitates the identification of criminals in case of theft.
- Constant monitoring and incident response: ATM networks must be constantly monitored by security operations centers, capable of promptly identifying any anomalies, suspicious activities, or security incidents. In case of an incident, it is fundamental to have an effective response plan to limit damage, restore ATM functionality, and investigate the occurrence to prevent future attacks.
- Strong authentication and access control: Implementing strong authentication systems for access to ATM systems, both at the physical level (e.g., with badges and electronic keys for technical staff) and logical level (e.g., with complex passwords and two-factor authentication for remote access). Access control must be rigorous and based on the principle of least privilege, granting only the accesses strictly necessary to perform one’s duties.
- Penetration testing and vulnerability assessment: Conducting regular penetration tests and vulnerability assessments on ATMs allows for the preventive identification of vulnerabilities in the system and verification of its resistance to cyberattacks. These tests must be conducted by external and independent security experts, capable of simulating real attacks and providing concrete recommendations to improve security.
- Staff training and awareness: The training and awareness of the technical and security staff managing ATMs are fundamental to ensuring the effectiveness of all security measures. Staff must be adequately trained on existing threats, security procedures to follow, and incident response methods.
System-side security measures are complex and costly, but they represent an indispensable investment to protect ATMs and maintain customer trust in the banking system.
User-Side Security Measures: Awareness and Prudence at the ATM
We users, too, as we have seen, can do our part to improve ATM security and protect our money. Adopting prudent behaviors and paying attention to our surroundings are simple but effective actions to reduce risks and prevent scams and thefts.
Here is a handbook of user-side security measures to put into practice every time we use an ATM:
- Choose safe ATMs: Prioritize internal ATMs at bank branches or ATMs located in crowded public places, well-lit, and video-monitored. Avoid isolated, poorly lit ATMs or those located in peripheral areas, especially during night hours.
- Observe the ATM carefully: Before inserting the card, check for signs of tampering on the shutter, keypad, or surrounding area. Check for suspicious devices superimposed or anomalies in the ATM’s appearance. In case of doubt, do not use the ATM and report the situation to the bank or authorities.
- Protect the PIN: Always cover the keypad with your hand while typing the PIN, preventing prying eyes or hidden micro-cameras from recording it. Use your other hand or wallet to create an effective barrier.
- Do not get distracted: While using the ATM, concentrate on the operation and do not get distracted by people approaching or talking to you. Criminals can use distraction as a technique to steal the PIN or card.
- Do not accept help from strangers: Do not ask for and do not accept help from strangers to use the ATM. If you have difficulties, ask bank staff or contact your bank’s customer service by phone.
- Always take the receipt: Always take the receipt of the operation and keep it to check the bank statement and verify the correctness of transactions. Do not throw the receipt in the bin near the ATM, but take it with you and destroy it securely once checked.
- Do not count money in public: After withdrawing cash, put it immediately in your wallet or bag and do not count money in public, attracting the attention of potential malicious actors.
- Guard your card carefully: Never leave the card unattended and never communicate the PIN to anyone, not even family or friends. Memorize the PIN and destroy the paper on which you may have written it down.
- Activate bank notifications: Activate SMS or email notification services from your bank to be alerted in real-time of every transaction made with your card. This allows you to promptly identify any suspicious transactions and block the card immediately.
- Regularly check your bank statement: Regularly check your bank statement and card movements, promptly reporting any unauthorized transactions or anomalies to the bank.
By adopting these simple but important security measures, we can protect ourselves and contribute to making ATMs a safer environment for everyone.
Comparative Table: ATM Weaknesses and Countermeasures
| Weak Point | Description | System-Side Countermeasures | User-Side Countermeasures |
|---|---|---|---|
| Obsolete Software | Software not updated with security patches, vulnerable to malware attacks. | Timely software updates, security patches, antivirus, IDS. | No direct action, but awareness of the importance of system security. |
| Vulnerable Hardware | ATM physically tamperable, shutter forceable, skimming devices installable. | Armoring, alarms, video surveillance, strategic positioning, ink staining systems. | Choose safe ATMs, observe the ATM carefully before use, report anomalies. |
| Insecure Networks | Interceptable communications, weak protocols, insufficient encryption. | Secure communication protocols, robust encryption, VPN, constant network monitoring. | No direct action, but awareness of risks related to insecure networks. |
| Skimming and Shimming | Theft of card data via devices installed on the ATM. | Hardware and software anti-skimming measures, anomaly detection, periodic ATM checks. | Observe the ATM carefully, check slot and keypad, protect PIN entry. |
| Shoulder Surfing | Theft of PIN via direct observation during entry. | Strategic ATM positioning, privacy screens, design obstructing side view. | Choose safe ATMs, pay attention to surrounding people, always protect PIN entry. |
| Physical Attacks and Robberies | Forcing ATM, explosions, armed robberies to steal cash or card. | Advanced physical security, alarms, video surveillance, rapid law enforcement response. | Choose safe ATMs, pay attention to surroundings, do not react in case of robbery, call 112 and block the card. |
Conclusions

ATM security is a complex and constantly evolving topic that requires a multidisciplinary approach and constant commitment from all actors involved: ATM network operators, financial institutions, law enforcement, and, last but not least, us users.
We have seen how ATM weak points are numerous and varied, ranging from software and hardware vulnerabilities to communication network fragilities, up to risks related to human behavior. But we have also highlighted how there are numerous countermeasures and best practices capable of strengthening ATM security and protecting users from threats.
Technology plays a fundamental role in protecting ATMs, with increasingly sophisticated software updates, antivirus, encryption, advanced physical security, and monitoring systems. But technology alone is not enough. Constant vigilance, periodic checks, penetration tests, and timely response to incidents are necessary to ensure an adequate level of security.
And then there is us users, the final link in the security chain. Our behavior, our attention, and our awareness can make the difference between being victims or protected users. Choosing safe ATMs, carefully observing the surrounding environment and the machine itself, always protecting PIN entry, not getting distracted, and regularly checking the bank statement are simple but powerful actions to defend our money and prevent scams and thefts.
In an increasingly digitized and interconnected world, ATM security remains an absolute priority. Collaboration between all actors, technological innovation, and user awareness are the paths to follow to guarantee a safer future for our money and our financial peace of mind. Let us always remember that security is a journey, not a destination, and requires constant commitment and continuous attention.
Frequently Asked Questions

The main risks are skimming and shimming (theft of card data), shoulder surfing (theft of the PIN), physical attacks, and robberies.
Observe the ATM carefully, check for anomalies, protect the keypad while typing the PIN, and use internal ATMs if possible.
Immediately block the card, contact your bank, and report the incident to the competent authorities.
ATMs are generally safe, but they present vulnerabilities. Security depends on both the measures adopted by operators and user behavior.
Banks implement various security measures, including software updates, antivirus, encryption, advanced physical security, and constant monitoring.
Choose safe ATMs, observe the ATM carefully, protect the PIN, do not get distracted, and regularly check your bank statement.
Yes, ATMs inside bank branches are generally safer than external ATMs.
Shimming is a data theft technique similar to skimming, but it targets EMV chip cards by intercepting chip data.
Shoulder surfing is the technique of stealing the PIN by secretly observing the user while they type it on the ATM keypad.
Do not react, do not resist, hand over the cash and card to the robbers, call 112, and block the card.



Did you find this article helpful? Is there another topic you'd like to see me cover?
Write it in the comments below! I take inspiration directly from your suggestions.