Every day our inbox handles work communications, personal messages and, unfortunately, scam attempts too. Faced with a suspicious email announcing a prize win or requesting urgent action, the first reaction is doubt. There is a tool, often ignored, that allows you to go beyond appearances and analyze the true nature of a message: the ‘Show Original’ function. This command opens the doors to the email’s source code, a technical text that hides precious information about its origin and authenticity. Understanding how to read it is not a skill reserved only for IT experts, but a practical competence for anyone wishing to navigate the digital world more securely.
Think of this function as the “behind the scenes” of every email we receive. While our email client interface shows us a clean and tidy message, the source reveals the infrastructure that transported it. By analyzing the email header, i.e., the technical heading, we can discover the path it took and verify if the person claiming to have sent it is really who we think they are. This analysis is fundamental for unmasking phishing attempts and other threats, transforming a simple user into a conscious and prepared digital detective.
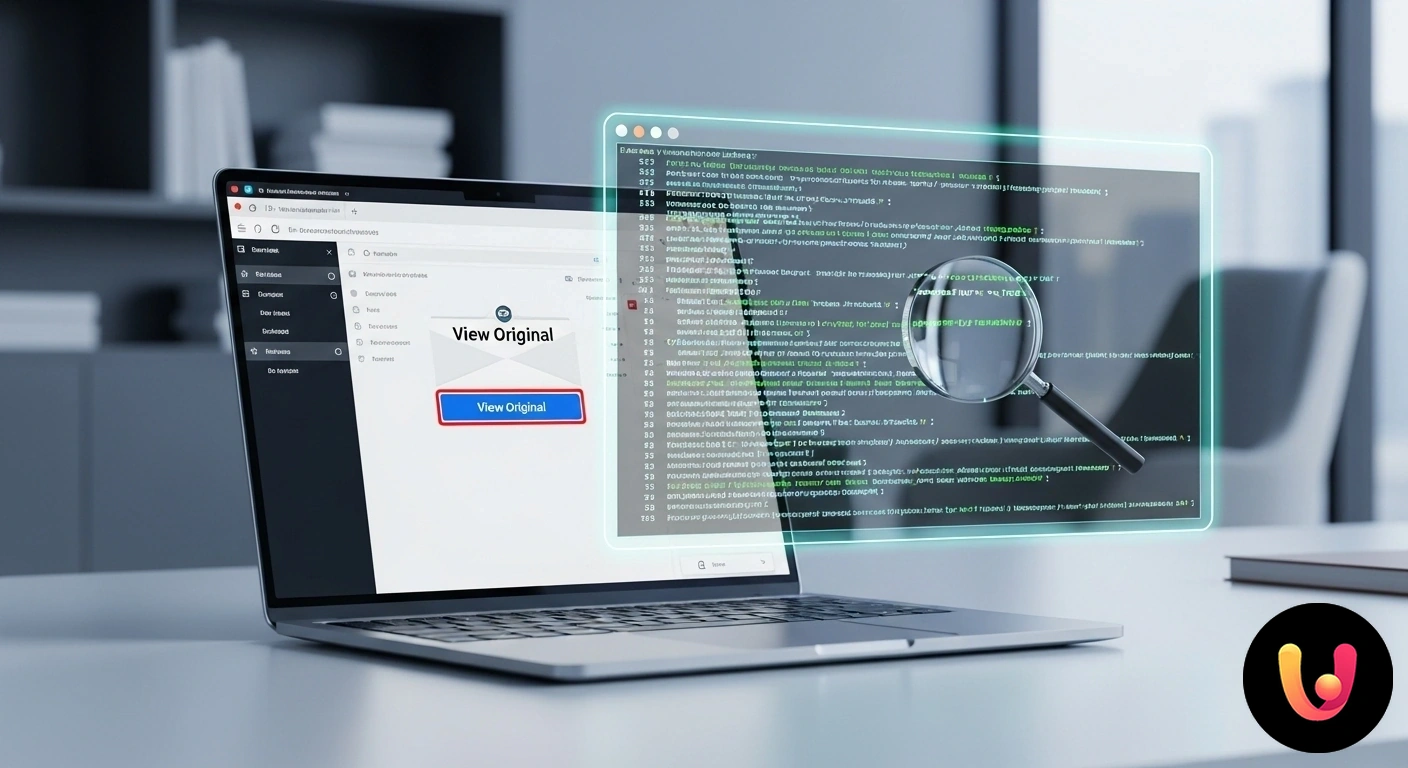
What is the ‘Show Original’ Function
The ‘Show Original’ function, or ‘View Source’, is an option available in most email programs that allows access to the raw text of an email. Instead of displaying the message formatted with images, buttons, and stylized text, this tool shows the complete code that composes it. We can imagine it as the X-ray of a letter: while the naked eye sees only the written text, the X-ray reveals the texture of the paper, the composition of the ink, and the fingerprints left along the way. Similarly, an email’s source contains not only the visible content but also a series of metadata and fundamental technical instructions.
The content of the source is mainly divided into two parts. The first is the header, a section that tracks the email’s journey from the sender’s server to the recipient’s. The second is the body, which contains the actual message, often in different formats like plain text and HTML. The latter is the code that defines the graphic appearance of the email, such as colors, layout, and images. Accessing this information is the first step for a thorough technical analysis, essential for security and troubleshooting.
Why It Is Important: A Balance Between Tradition and Innovation
In the Italian and Mediterranean cultural context, communication is often founded on trust and interpersonal relationships. This tradition, based on human contact, clashes with the impersonal nature of the digital world, where technological innovation has created new forms of interaction but also new threats. Email, now a “traditional” tool of our digital life, requires an approach that combines the prudence typical of our culture with a new technical awareness. The ‘Show Original’ function perfectly embodies this balance: it is an innovative tool that allows us to apply healthy skepticism, a sort of digital “street smarts,” to protect ourselves.
Data on cybercrime in Europe and Italy is constantly growing. According to recent statistics, millions of Italians are targets of phishing attempts every year, with increasingly sophisticated techniques. In this scenario, knowing how to analyze an email is no longer a quirk for technology enthusiasts, but a practical necessity. It becomes a gesture of digital self-defense that strengthens our autonomy and allows us to distinguish legitimate communications from traps. Adopting this mindset means evolving, bringing the traditional attention to human relationships into the digital domain to navigate with greater safety.
Practical Guide: How to Find ‘Show Original’
Accessing an email’s source is a simple operation, although the procedure varies slightly depending on the email client used. Knowing the steps for the most common services allows you to have this powerful tool always at hand. Here is how to find it on the main providers:
- Gmail: Open the email you want to analyze. At the top right of the message, click on the icon with the three vertical dots (More). In the dropdown menu that appears, select ‘Show original’. A new browser tab will open with the entire source of the email.
- Microsoft Outlook (web version and desktop app): Open the message in a separate window. In the menu bar at the top, look for the icon with three dots or the ‘Actions’ section. From there, select ‘View’ and then ‘View message source’. The source will appear in a new window.
- Apple Mail: Select the email you are interested in. From the menu bar at the top of the screen, click on ‘View’. In the dropdown menu, go to ‘Message’ and finally choose ‘Raw Source’. The raw code of the message will be shown in a new window.
Once the source is opened, you will be faced with a block of text that may seem incomprehensible at first glance. Do not be intimidated: the next step is learning to recognize the key information hidden within it.
Deciphering the Header: Hidden Information
An email’s header is its digital ID card and the timeline of its journey. Reading it correctly, starting from the bottom up, allows you to reconstruct the message’s path and verify its authenticity. One of the most important sections is ‘Received’, which shows every server through which the email has passed. If an email apparently sent by your bank comes from a server with a strange name or located in an unexpected country, it is a strong warning sign. Another fundamental line is ‘Authentication-Results’. Here you find the results of security checks like SPF, DKIM, and DMARC. These protocols verify if the server that sent the email was authorized to do so for that domain. A “fail” or “softfail” result indicates that the message might be forged.
By analyzing the header, it is also possible to identify discrepancies between the displayed sender (‘From’ field) and the actual address from which the communication originated (often traceable in the ‘Return-Path’ or ‘Reply-To’ fields). Scammers often mask the real address to deceive the recipient. Learning to spot these inconsistencies is one of the most effective skills for protecting oneself. Reading the header transforms an email from simple text into a rich source of data for a personal digital investigation.
Practical Use Cases: When to Use ‘Show Original’
Theory is useful, but practical examples show the true power of this tool. Imagine receiving an email from a courier notifying you of a package on hold, asking you to click a link to release it. The appearance is professional, but something doesn’t add up. Using ‘Show Original’, you notice in the ‘Received’ field that the email does not come from the courier’s official servers, but from an unknown IP address. You have just unmasked a phishing attempt. This is just one of many scenarios where this function proves decisive.
Another common case is a fake bank communication signaling anomalous access to your account. Before panicking, open the source. The analysis of the ‘Authentication-Results’ field shows that the DKIM and SPF checks failed: ‘dkim=fail’, ‘spf=fail’. This is technical proof that the email is a fake, an attempt to recognize a phishing attempt to steal your credentials. Finally, if a newsletter you care about ends up directly in spam, the header can reveal the reason, showing potential configuration problems on the sender’s server that compromise its reputation and deliverability.
Beyond Security: Other Benefits
Although security is the main field of application, the ‘Show Original’ function offers advantages in other contexts too. Sometimes, an email may appear “broken”: images not loading, misaligned text, or incomprehensible characters. This often happens due to poorly written HTML code or code incompatible with your email client. By analyzing the source, a user with minimal familiarity can identify the cause of the problem, such as a link to a non-working image or an incorrectly closed HTML tag.
Furthermore, the message body in the source almost always contains a plain text version alongside the HTML one. If the formatted version is unreadable, the text version might still be perfectly clear, allowing you to retrieve the essential information of the message. Finally, for the curious, exploring an email’s source is a fascinating way to understand the workings of one of the internet’s longest-lived and most fundamental technologies. It is an opportunity to appreciate the complexity hidden behind a daily gesture like sending and receiving an email message.
In Brief (TL;DR)
The ‘Show Original’ function is a powerful tool that reveals technical details hidden in every email, allowing you to analyze headers, source code, and security for in-depth analysis.
Analyzing an email’s source code is essential for diagnosing delivery issues and verifying the sender’s authenticity, protecting you from phishing and spam.
Mastering this function allows you to diagnose delivery problems and unmask phishing or spoofing attempts.
Conclusions

The ‘Show Original’ function is much more than a simple option for insiders. It is a tool of transparency and control that gives power back to the user, allowing them to independently verify the origin and reliability of the communications they receive. In an era where digital threats like phishing are becoming increasingly insidious, knowing how to read the hidden information in an email is a precious skill. It does not require professional IT knowledge, but just a bit of curiosity and the willingness to look beyond the surface.
Adopting the habit of inspecting suspicious emails through their source is a concrete step towards greater digital security. It means combining prudence, a value rooted in our culture, with the tools that innovation makes available to us. Knowing how to decipher a header not only protects us from scams but also makes us more aware and autonomous users, capable of navigating the digital world with the same wariness we use in everyday life. After all, online safety starts with a simple gesture: a click on ‘Show Original’.
Frequently Asked Questions

Yes, it is a completely safe operation. The ‘Show Original’ function opens a text-only view of the email’s source code. It does not execute scripts, download images, or activate any potentially harmful content. It is the digital equivalent of reading the ingredient label of a product: it simply shows the technical information of the message you have already received.
They are three fundamental security protocols for email authentication, working together to verify that an email actually comes from the domain it claims to come from. In simple terms: – **SPF (Sender Policy Framework)** is a list of servers authorized to send emails on behalf of a certain domain. – **DKIM (DomainKeys Identified Mail)** adds a digital signature to the email, ensuring that the content has not been altered during transit. – **DMARC (Domain-based Message Authentication, Reporting, and Conformance)** tells the receiving server what to do if the SPF or DKIM checks fail (for example, whether to put the message in spam or reject it). A ‘pass’ result for these checks is an excellent indicator of legitimacy.
Not always precisely. The headers, particularly the ‘Received’ fields, show the IP addresses of the mail servers through which the message passed, read from bottom to top. This can give you an idea of the country or provider of origin, but often the visible IP is that of a large service (like Google or Microsoft) and not that of the sender’s personal device. Furthermore, the use of VPNs or corporate networks can mask the real location. So, it is a useful clue, but not definitive proof.
The technical aspect can be intimidating, but you don’t need to understand everything. Focus on a few key elements using the browser’s search function (Ctrl+F or Cmd+F). Search for ‘Authentication-Results’ to see the outcome of SPF, DKIM, and DMARC security checks. Examine the ‘From’, ‘Return-Path’, and ‘Reply-To’ fields: if they are very different from each other, it is a warning sign. Finally, read the ‘Received’ fields from bottom to top to trace the server path.
In most cases, email applications for smartphones (like Gmail or Outlook for iOS/Android) do not include the ‘Show Original’ function to keep the interface simple. To access the full source code of an email, it is almost always necessary to access your mailbox via a web browser on a desktop or laptop computer. Once logged in, you can follow the standard procedure for your provider, such as clicking on the three-dot menu in Gmail and selecting ‘Show original’.



![Blocking Emails on Gmail: The Guide to Freeing Yourself from Spam. Gmail user interface showing the dropdown menu of an email with the option 'block [sender name]' highlighted.](https://blog.tuttosemplice.com/wp-content/uploads/2025/07/generated_images_6_b6c18987-1024x559.webp)
Did you find this article helpful? Is there another topic you'd like to see me cover?
Write it in the comments below! I take inspiration directly from your suggestions.