In Brief (TL;DR)
Financial institutions must adopt hybrid cloud architectures to ensure data sovereignty and compliance with DORA and GDPR regulations.
Advanced protection requires the use of customer-managed cryptographic keys and Confidential Computing technologies to armor sensitive data during processing.
Network isolation via private connections and immutable log management ensure the operational resilience needed to pass audits and prevent attacks.
The devil is in the details. 👇 Keep reading to discover the critical steps and practical tips to avoid mistakes.
In the financial landscape of 2026, fintech cloud security represents the fundamental pillar upon which investor trust and regulatory compliance rest. With the full implementation of the DORA (Digital Operational Resilience Act) regulation and the continuous evolution of GDPR, financial institutions can no longer limit themselves to migrating to the cloud: they must architect environments that ensure data sovereignty and operational resilience. This technical guide explores the configuration of secure hybrid architectures, focusing on cryptographic key management (CMK), Confidential Computing, and log immutability for forensic purposes.

1. The Hybrid Cloud Dilemma in Fintech: Compliance and Agility
Banks and Fintech companies operate in a “zero risk” context. Adopting a Hybrid Cloud architecture allows critical data (Core Banking, high-risk PII) to be kept on on-premise infrastructure or Private Cloud, while leveraging the scalability of Public Clouds (AWS, Google Cloud, Azure) for processing and analysis. However, the challenge lies in data segregation.
According to Article 32 of the GDPR, security of processing must include pseudonymization and encryption. In a hybrid context, this means that data must never travel in clear text between the local data center and the public cloud.
2. Encryption and Key Management (CMK): BYOK in Practice
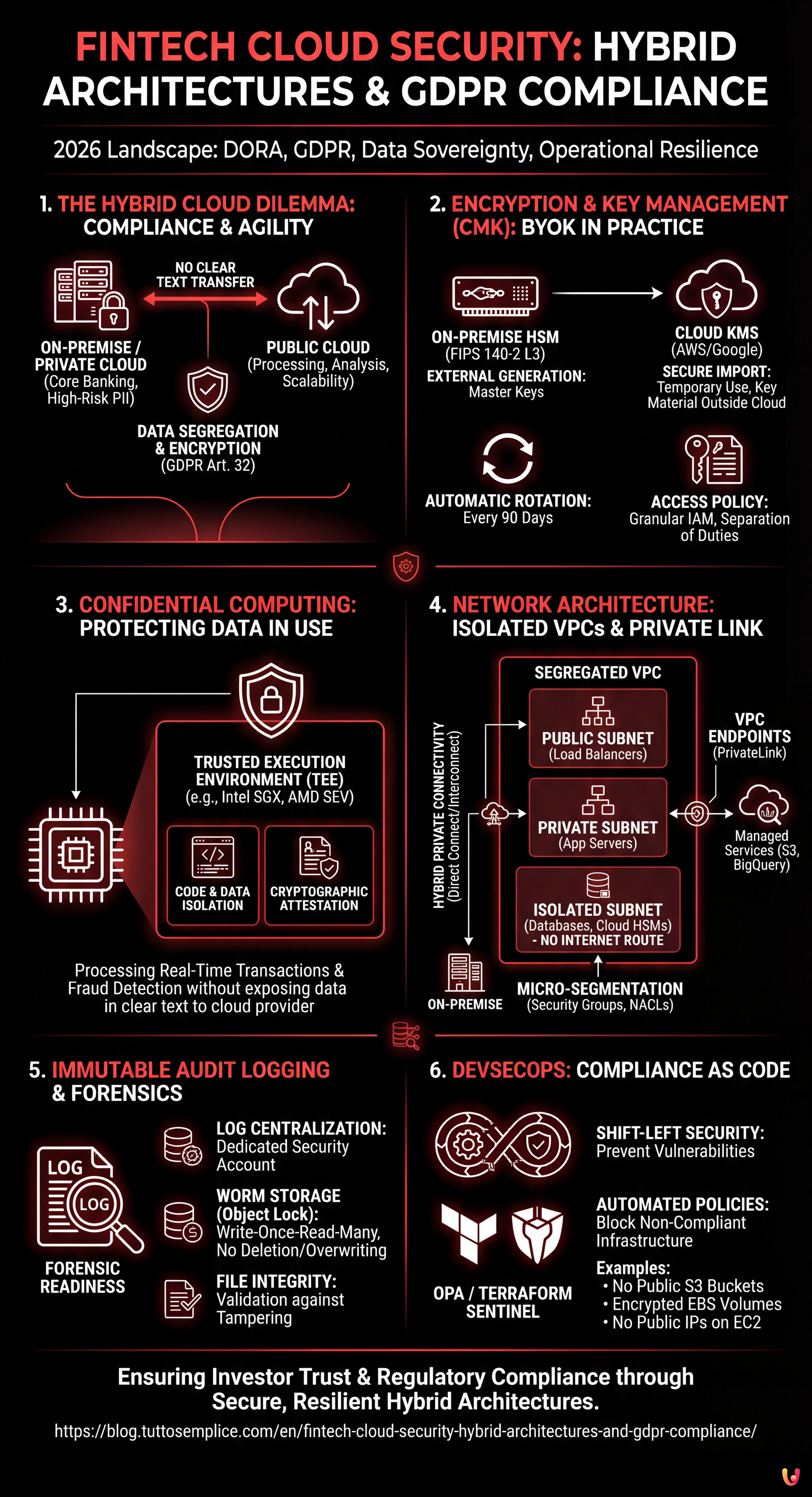
For a financial institution, relying on encryption keys managed by the cloud provider (Platform Managed Keys) is not sufficient. The best practice, which has become the de facto standard, is the use of Customer Managed Keys (CMK), often in a Bring Your Own Key (BYOK) scenario.
Configuration on AWS KMS and Google Cloud KMS
The goal is to maintain exclusive control over the key lifecycle. Here is how to structure secure management:
- External Generation: Master keys are generated within an on-premise HSM (Hardware Security Module) certified to FIPS 140-2 Level 3.
- Secure Import: The key is imported into the provider’s KMS (e.g., AWS KMS) only for temporary use, keeping the original “key material” outside the cloud.
- Automatic Rotation: Configure key rotation policies every 90 days (or fewer, according to internal policies), ensuring that old data remains decryptable while new data is encrypted with the new key version.
- Access Policy (Key Policy): Define granular IAM policies that separate those who can administer the keys from those who can use them for cryptographic operations.
3. Confidential Computing: Protecting Data in Use

Until a few years ago, data was vulnerable during processing (in use) in RAM. Today, Confidential Computing is an essential requirement for fintech cloud security when processing real-time transactions or running fraud detection algorithms on unencrypted data.
This technology uses Trusted Execution Environments (TEE) or secure “enclaves” (such as Intel SGX or AMD SEV) supported by major cloud providers. Within these enclaves:
- Code and data are isolated from the host operating system and hypervisor.
- Not even the cloud provider administrator can access the enclave memory.
- A cryptographic attestation is generated proving that the running code is exactly what was authorized and has not been altered.
For a Fintech, this means being able to run Machine Learning models on sensitive customer data in the public cloud without ever exposing the data in clear text to the underlying platform.
4. Network Architecture: Isolated VPCs and Private Link
Network configuration is the first line of defense. In a hybrid architecture for financial data, public exposure must be zero for backends.
Best Practices for VPC Segregation
- Subnet Tiering: Creation of public subnets (only for Load Balancers), private subnets (for Application Servers), and isolated subnets (for Databases and Cloud HSMs). Isolated subnets must not have routes to the Internet Gateway.
- Hybrid Private Connectivity: Exclusive use of AWS Direct Connect or Google Cloud Interconnect for traffic between on-premise and cloud. Traffic must never transit over the public internet.
- VPC Endpoints (PrivateLink): To access managed services (such as S3 or BigQuery) from private subnets, use VPC endpoints. This ensures traffic remains within the provider’s network, avoiding exit to the internet.
- Micro-segmentation: Implementation of Security Groups and Network ACLs that allow traffic only on strictly necessary ports (e.g., port 443 only from Load Balancer to App Server).
5. Immutable Audit Logging and Forensics
In the event of an incident or banking audit, traceability is everything. Logs must not only be collected but must be immutable to ensure forensic validity.
Implementing “Forensic Readiness”
A robust configuration includes:
- Log Centralization: All logs (CloudTrail, VPC Flow Logs, Application Logs) are sent to a dedicated and segregated security account.
- Write-Once-Read-Many (WORM): Use of storage with Object Lock (e.g., AWS S3 Object Lock in Compliance mode). This prevents deletion or overwriting of logs for a defined period (e.g., 7 years for banking regulations), even by the root account.
- File Integrity: Activation of Log File Validation to mathematically detect any tampering attempt.
6. DevSecOps: Compliance as Code
Security cannot be entrusted to manual controls. In a modern Fintech environment, compliance must be codified in CI/CD pipelines.
Using tools like Open Policy Agent (OPA) or Terraform Sentinel, it is possible to block the deployment of non-compliant infrastructure. Examples of blocking policies:
- “No S3 bucket can be public.”
- “All EBS volumes must be encrypted with the project-specific CMK.”
- “EC2 instances cannot have public IP addresses.”
This approach shifts security to the left (Shift-Left Security), preventing vulnerabilities before they reach production.
Conclusions

Ensuring fintech cloud security requires a holistic approach that goes beyond a simple firewall. The integration of customer-managed encryption, confidential execution environments, and immutable logs creates a defense-in-depth architecture capable of withstanding advanced threats and satisfying the most demanding auditors. For CTOs and Security Architects, the focus must shift from simple perimeter protection to intrinsic data protection, wherever it resides.
Frequently Asked Questions

Confidential Computing is an advanced technology that protects data during processing in RAM, using secure enclaves isolated from the operating system. This approach is fundamental for financial institutions as it allows sensitive data analysis and fraud detection in the public cloud without ever exposing the information in clear text to the cloud service provider.
The best strategy consists of the Bring Your Own Key (BYOK) model using Customer Managed Keys (CMK). Master keys are generated in on-premise hardware security modules and imported only temporarily into the cloud, ensuring that the bank maintains exclusive control over the encryption lifecycle and can revoke access at any time.
It is necessary to implement rigorous segmentation via isolated VPCs and private subnets that do not have direct internet access. Traffic between the local data center and the cloud must travel exclusively over dedicated connections like Direct Connect or Interconnect, while managed services must be reached via private endpoints to avoid transit over the public network.
Immutable logs, protected via WORM (Write Once Read Many) technologies, ensure that audit trails cannot be modified or deleted, even by system administrators. This feature is essential for forensic readiness and allows for demonstrating complete data integrity to auditors in the event of incidents or regulatory checks.
DevSecOps integrates security controls directly into the infrastructure code, automatically blocking the release of non-compliant resources via CI CD pipelines. Through automated policies, it is possible to prevent critical human errors such as creating public archives or using unencrypted volumes, ensuring preventive security from the earliest stages of development.
Sources and Further Reading

- Regulation (EU) 2022/2554 (DORA) – Digital Operational Resilience Act
- General Data Protection Regulation (GDPR) – Official Legal Text
- NIST FIPS 140-2: Security Requirements for Cryptographic Modules
- European Banking Authority (EBA) Guidelines on Outsourcing Arrangements
- NIST Special Publication 800-207: Zero Trust Architecture
- NIST IR 8320: Hardware-Enabled Security for Cloud and Edge Computing (Confidential Computing)



Did you find this article helpful? Is there another topic you'd like to see me cover?
Write it in the comments below! I take inspiration directly from your suggestions.