Imagine a bank robber who breaks into a vault, bypasses the gold bars and cash, and instead steals a stack of documents written in a language that no human being has spoken for a thousand years. To the police, this behavior seems irrational. The documents are indecipherable; they are, for all intents and purposes, worthless gibberish. But the robber knows something the authorities do not: a Rosetta Stone is being built, and once it is finished, those useless papers will topple governments. This is not the plot of a science fiction novel. It is the reality of a cybersecurity phenomenon known as Harvest Now, Decrypt Later (HNDL), and it is currently the single most terrifying strategy being deployed by state-sponsored actors and criminal syndicates across the globe.
In the fast-paced world of tech, we are accustomed to immediate threats: ransomware that locks screens instantly, phishing emails that demand urgent clicks, or denial-of-service attacks that crash websites in seconds. However, the Harvest Now, Decrypt Later strategy operates on a completely different timeline. It is a patient, silent war where the loot is encrypted data that cannot currently be cracked. The attackers are betting on the inevitability of scientific innovation—specifically, the arrival of fault-tolerant quantum computers—to unlock these digital time capsules in the future. As we stand here in early 2026, the industry is waking up to the realization that our current defenses are protecting us from today’s burglars, but leaving the door wide open for tomorrow’s archaeologists of secrets.
The Mechanics of the Invisible Theft
To understand why HNDL is such a potent threat, we must first bridge the curiosity gap regarding how digital secrecy works. Today, the security of the internet—from your WhatsApp messages to nuclear launch codes—relies largely on public-key cryptography, such as RSA and Elliptic Curve Cryptography (ECC). These systems are based on complex mathematical problems, typically involving the factoring of massive prime numbers. For a classical supercomputer, solving these problems is like trying to find a specific grain of sand on a beach; it would take millions of years.
When hackers intercept this data today, they see nothing but random noise. A file containing a top-secret trade secret looks exactly like a file containing random static. Under normal circumstances, this data would be discarded as useless. However, under the HNDL doctrine, storage is cheap and bandwidth is plentiful. Attackers are scraping terabytes of this encrypted traffic and storing it in massive data centers. They are not trying to read it now. They are archiving it, tagging it, and waiting. They are banking on the fact that the mathematical shield protecting this data has an expiration date.
The Quantum Key: When Math Breaks
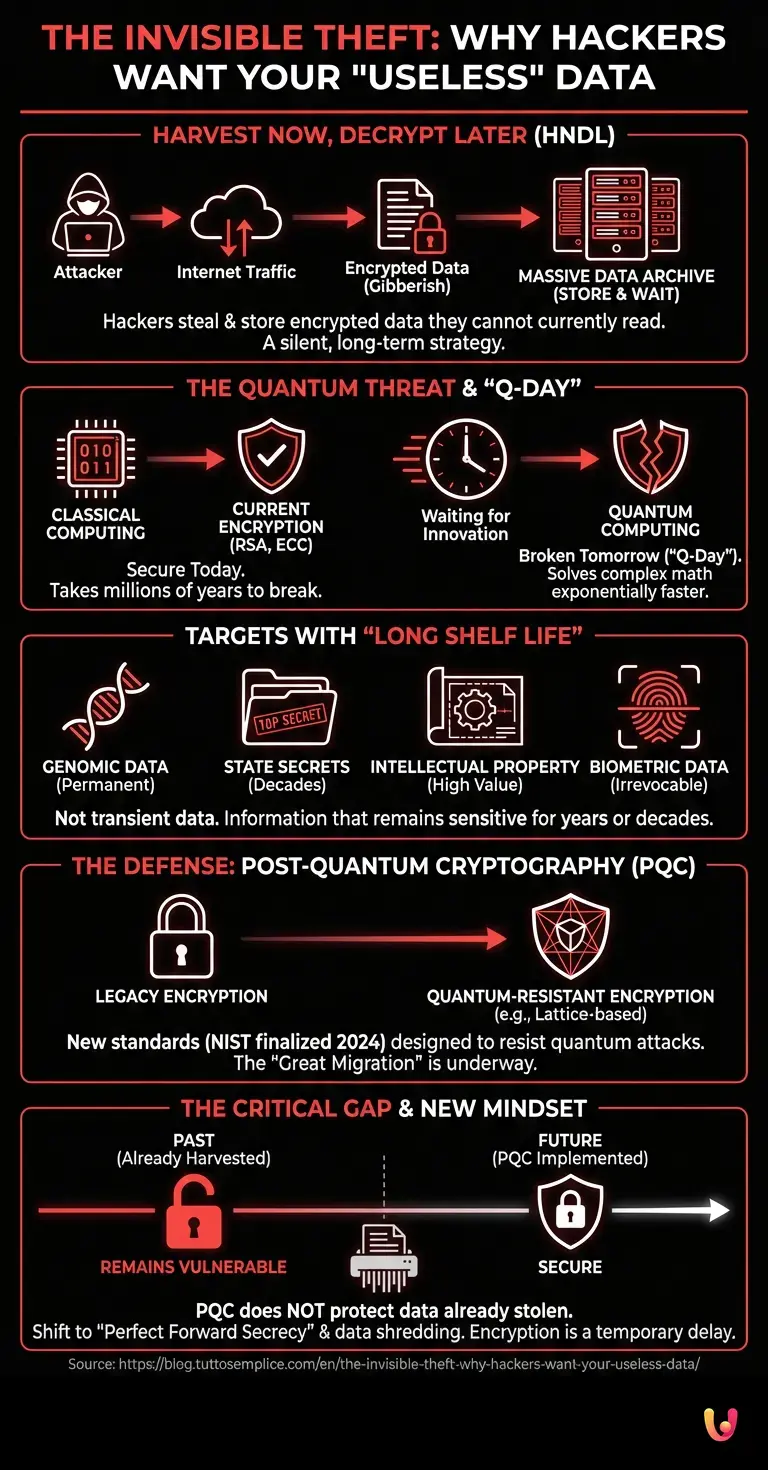
The “Rosetta Stone” that these attackers are waiting for is the quantum computer. Unlike classical computers, which process bits as either 0s or 1s, quantum computers utilize qubits that can exist in a state of superposition. This allows them to perform certain calculations exponentially faster than their silicon-based ancestors. In the 1990s, mathematician Peter Shor developed an algorithm (Shor’s Algorithm) that proved a sufficiently powerful quantum computer could factor those massive prime numbers with terrifying ease.
In 2026, we are edging closer to what experts call “Q-Day”— the moment a quantum computer becomes powerful enough to break current encryption standards. While we are not quite there yet, the timeline has accelerated. Startups and tech giants are racing to build stable quantum processors. While this is a triumph for scientific innovation, it is a nightmare for cybersecurity. Once Q-Day arrives, the encryption that protects the data harvested today will dissolve. The “gibberish” stored in the hackers’ servers will instantly translate into plain text. The vault will open.
What Is Worth Waiting For?

You might wonder: “If they decrypt my credit card number in ten years, who cares? It will be expired by then.” This is a valid point for transient data. The HNDL strategy is not interested in your Netflix password or your current credit card details. The targets are information classes with a “long shelf life.”
Consider the following categories of data that remain sensitive for decades:
- Genomic Data: Your DNA sequence does not change. If your genetic data is harvested today, it will still be yours—and potentially used against you or your descendants—in 2040.
- State Secrets and Intelligence: Diplomatic cables, identities of undercover operatives, and military blueprints often remain classified and sensitive for 25 to 50 years.
- Intellectual Property: The formula for a pharmaceutical drug or the design of an advanced aircraft engine represents billions of dollars in R&D. Even ten years later, revealing these secrets could destroy a company’s competitive advantage.
- Biometric Data: Fingerprints and retinal scans are permanent identifiers. Once compromised, they cannot be reset like a password.
For nation-states engaged in long-term strategic competition, HNDL is the ultimate investment. They are capturing the world’s secrets today to gain leverage in the geopolitical landscape of the 2030s.
The Race for Immunity: Post-Quantum Cryptography
The tech industry has not been sitting idly by. Recognizing this threat, the global cryptographic community has been working on a solution known as Post-Quantum Cryptography (PQC). These are new encryption methods based on different types of mathematics—such as lattice-based cryptography—that are resistant even to quantum computers.
In 2024, the U.S. National Institute of Standards and Technology (NIST) finalized the first set of PQC standards (including algorithms with names like CRYSTALS-Kyber and CRYSTALS-Dilithium). Now, in 2026, we are in the midst of the “Great Migration.” Startups specializing in crypto-agility are emerging to help corporations swap out their old encryption engines for these new, quantum-resistant ones. It is akin to changing the foundation of a skyscraper while people are still working inside it.
However, this migration does not solve the problem of data that has already been harvested. If an attacker stole your encrypted health records in 2023, upgrading your hospital’s encryption in 2026 does nothing to protect that stolen file. The thief still has it, and they are still waiting for the quantum key. This creates a strange paradox where the damage is done, but the wound hasn’t appeared yet.
The Role of AI in the Silent War
Artificial Intelligence plays a dual role in this narrative. On one hand, AI is accelerating the development of quantum computing, helping physicists optimize qubit stability and error correction. On the other hand, AI is being used to defend against HNDL. Advanced machine learning models are now being deployed to detect the specific traffic patterns associated with data harvesting.
Harvesting attacks often look different from standard data breaches. They are often “low and slow,” exfiltrating large volumes of encrypted data over long periods to avoid triggering alarms. AI-driven security systems are learning to recognize these subtle anomalies, flagging connections that are simply moving too much encrypted data to unknown servers. Furthermore, AI is assisting in the massive code refactoring required to implement PQC, scanning millions of lines of legacy code to identify where vulnerable encryption methods are hiding.
The Psychological Shift in Tech
The existence of HNDL forces a psychological shift in how we view technology and privacy. We have always assumed that if data is encrypted, it is safe. We treated encryption as a permanent wall. We now have to treat it as a temporary delay. This realization is driving a new wave of innovation focused on “Perfect Forward Secrecy” and information lifecycle management. Companies are learning that the best way to protect data from future decryption is to not store it at all, or to delete it immediately after use.
The “collect everything” mentality of the Big Data era is clashing with the liability of the Quantum era. Every byte of encrypted data you hoard is a potential future liability. Smart organizations are now shredding digital documents with the same fervor they used to digitize them.
In Brief (TL;DR)
Cybercriminals are hoarding unreadable encrypted data today, betting on future technology to unlock these digital secrets tomorrow.
The impending arrival of quantum computing threatens to shatter current encryption standards and expose this archived sensitive information.
This silent strategy specifically targets enduring assets like genomic records and state secrets that remain valuable for decades.
Conclusion

The “Harvest Now, Decrypt Later” phenomenon serves as a humbling reminder of the relentless march of technology. It challenges our perception of time and security, proving that a secret kept today is not necessarily a secret kept forever. While the general public worries about the visible disruptions of the digital age, the most profound battle is happening in the silence of server rooms, where encrypted packets are being stolen not for what they say today, but for what they will reveal tomorrow. As we navigate 2026 and beyond, the race is no longer just about building higher walls; it is about outrunning the future itself.
Frequently Asked Questions

The Harvest Now, Decrypt Later strategy, often abbreviated as HNDL, is a cyberattack method where hackers steal encrypted data that they cannot currently read. Instead of trying to crack the code immediately, they store this data in massive archives, waiting for future technological advancements. The attackers anticipate that the development of fault-tolerant quantum computers will eventually allow them to break current encryption standards, turning the stolen gibberish into readable sensitive information.
Quantum computing poses a significant threat to cybersecurity because it operates differently than classical computing. While traditional computers struggle to solve the complex mathematical problems protecting public-key cryptography like RSA, quantum machines use qubits and superposition to solve these problems exponentially faster. This capability means that once a sufficiently powerful quantum computer is built, it will be able to unlock the digital vaults protecting everything from state secrets to personal biometric data.
The data most at risk from HNDL attacks includes information with a long shelf life, rather than transient data like passwords or credit card numbers which expire quickly. Hackers prioritize stealing genomic data, biometric identifiers like fingerprints, intellectual property regarding trade secrets, and classified government intelligence. Since this information remains sensitive for decades, it provides long-term leverage for attackers who decrypt it years after the initial theft.
Post-Quantum Cryptography, or PQC, refers to new encryption methods designed to withstand the processing power of future quantum computers. Unlike current standards based on prime factorization, PQC relies on different mathematical foundations, such as lattice-based cryptography, which quantum machines cannot easily break. Organizations are currently migrating to these new standards to ensure that data encrypted today remains secure against the threats of tomorrow.
Unfortunately, implementing new encryption standards today cannot protect data that has already been harvested by attackers. If a hacker successfully exfiltrated encrypted files prior to a security upgrade, they possess a permanent copy of that data. The transition to Post-Quantum Cryptography only secures future communications and storage; it does not retroactively scrub stolen files from the servers of cybercriminals, leaving that historical data vulnerable to eventual decryption.





Did you find this article helpful? Is there another topic you'd like to see me cover?
Write it in the comments below! I take inspiration directly from your suggestions.