In Brief (TL;DR)
Financial data protection requires a Zero Trust architecture where identity replaces the traditional network perimeter.
Technical implementation involves using Service Mesh and mTLS to ensure secure and authenticated communications between cloud microservices.
Access controls must be granular, based on real-time context, and strictly follow the principle of least privilege.
The devil is in the details. 👇 Keep reading to discover the critical steps and practical tips to avoid mistakes.
In the cybersecurity landscape of 2026, the protection of sensitive data (PII) and financial information can no longer rely on traditional perimeter security models. Zero trust architecture (ZTA) has moved from being a buzzword to an essential industry standard, especially for financial institutions operating in cloud-native environments like AWS and Google Cloud. This technical guide explores how to design a robust ZTA, where trust is never implicit but must be continuously verified.

Introduction: The Paradigm Shift Towards Zero Trust
The traditional “castle-and-moat” model, which considered everything inside the corporate network safe, is obsolete. With a distributed workforce and microservices-based infrastructure, the perimeter is everywhere. According to NIST SP 800-207, zero trust architecture is founded on the principle “Never Trust, Always Verify”.
For the mortgage and credit sector, where the management of highly sensitive data is subject to stringent regulations, adopting a ZTA means shifting the focus from network security to the security of identity and the data itself. It is not just about installing a firewall, but orchestrating an ecosystem where every access request is authenticated, authorized, and encrypted.
Prerequisites and Technical Foundations
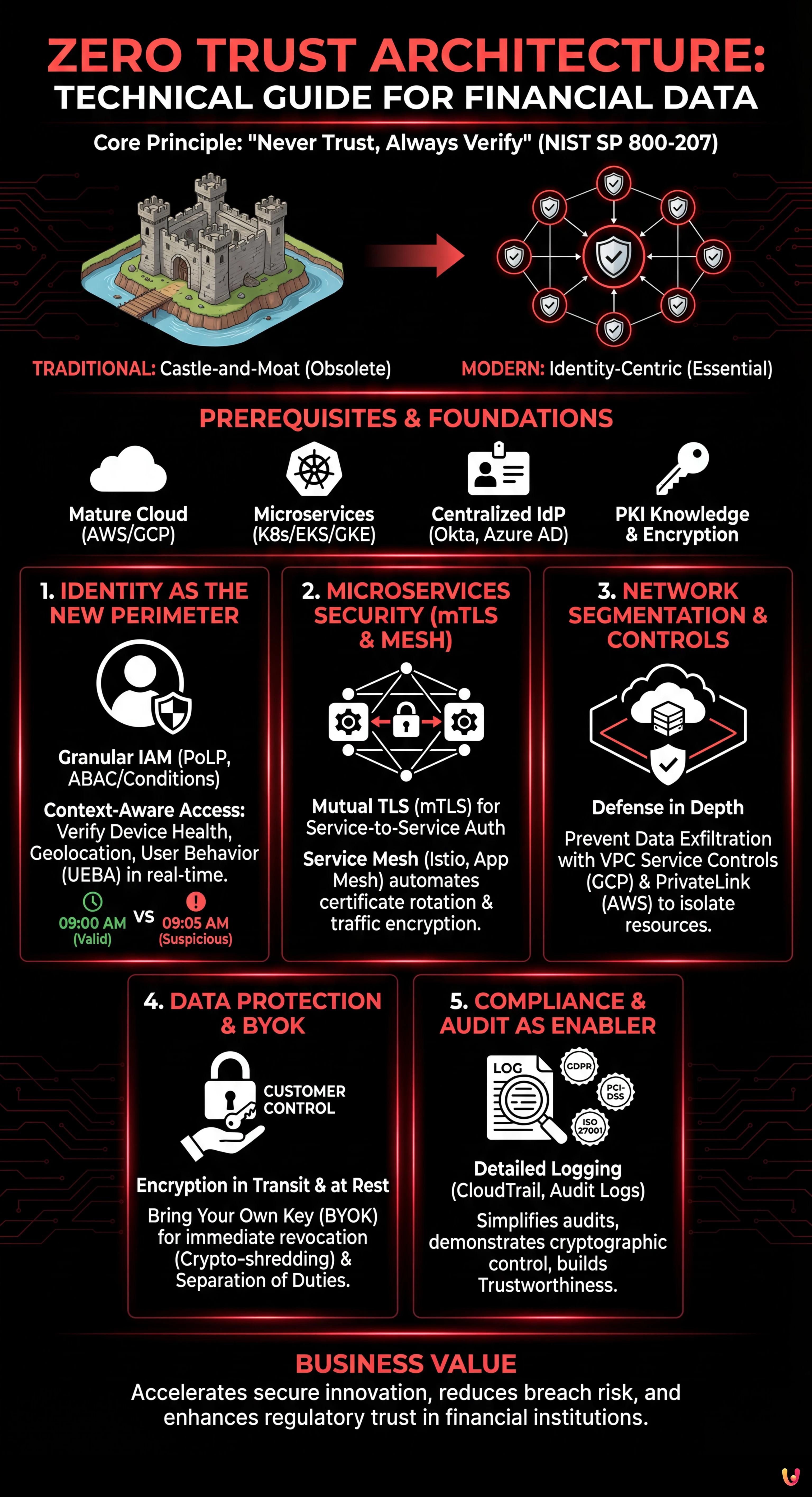
Before implementing an advanced ZTA, you must have:
- A mature cloud environment (AWS or Google Cloud Platform).
- A microservices architecture (Kubernetes/EKS/GKE).
- Centralized identity management (IdP) such as Okta, Azure AD, or AWS IAM Identity Center.
- Knowledge of asymmetric encryption principles and PKI (Public Key Infrastructure).
1. Identity as the New Security Perimeter

In a zero trust architecture, identity is the new firewall. Every actor (user or service) must possess a cryptographically verifiable identity.
Granular Access Management (IAM)
Using generic IAM (Identity and Access Management) roles is an unacceptable risk. On AWS and GCP, it is crucial to apply the Principle of Least Privilege (PoLP).
- AWS: Use Attribute-Based Access Control (ABAC). Instead of creating a role for every user, define policies based on tags (e.g.,
Project: MortgageApp,DataLevel: PII). This allows for dynamic scalability of permissions. - GCP: Leverage IAM Conditions to limit access to resources based on time, IP addresses, or device security status.
Context-Aware Access Policies
Authentication is not a one-off event. A valid request at 09:00 AM from a corporate laptop in Milan might become suspicious if repeated at 09:05 AM from an unknown device in Singapore. Modern systems must evaluate context in real-time:
- Device health status (patch level, presence of EDR).
- Geolocation and user behavior (UEBA).
- Sensitivity of the requested resource.
2. Microservices Security: mTLS and Service Mesh
In a cloud-native environment, microservices communicate constantly with each other. Assuming traffic within the VPC (Virtual Private Cloud) is secure is a fatal error.
Implementing mTLS (Mutual TLS)
The mTLS protocol ensures that not only does the client verify the server, but the server also verifies the client. This prevents Man-in-the-Middle attacks and service spoofing.
Implementing mTLS manually on every service is burdensome. The standard solution in 2026 involves using a Service Mesh like Istio (on GKE) or AWS App Mesh. The Service Mesh automatically handles:
- Rotation of short-lived certificates.
- Strong authentication between services (Service-to-Service auth).
- Encryption of traffic in transit without changes to application code.
Practical example: The “Credit Scoring” microservice will only accept connections from the “Mortgage Frontend” microservice if the latter presents a valid certificate signed by the Mesh’s internal CA, rejecting any other connection, even if it originates from the same subnet.
3. Network Segmentation and VPC Service Controls
Although identity is primary, network security remains a fundamental layer of defense (Defense in Depth).
VPC Service Controls (GCP) and PrivateLink (AWS)
To prevent Data Exfiltration, it is necessary to define service perimeters that isolate cloud resources.
- Google Cloud: VPC Service Controls allow you to define a perimeter around managed services (such as Cloud Storage or BigQuery). Even if a user has the correct credentials, if the request comes from outside the authorized perimeter, access is denied.
- AWS: Use AWS PrivateLink to expose services internally within the VPC without passing through the public internet, drastically reducing the attack surface.
4. Data Protection: Encryption and BYOK
For financial data, encryption is mandatory both in transit and at rest. However, in an advanced zero trust architecture perspective, whoever holds the keys holds the power.
Bring Your Own Key (BYOK)
Relying completely on keys managed by the cloud provider (e.g., AWS Managed Keys) may not be sufficient for certain compliance or data sovereignty requirements. The BYOK (or HYOK – Hold Your Own Key) approach involves the organization generating cryptographic keys in its own on-premise HSM (Hardware Security Module) or in a dedicated Cloud HSM, then importing them into the provider’s KMS.
Advantages of BYOK in the financial sector:
- Immediate Revocation: In the event of a cloud provider compromise or legal investigations, the company can revoke the master key, rendering the data in the cloud instantly unreadable (Crypto-shredding).
- Separation of Duties: Cloud administrators do not have access to decryption keys.
5. Compliance and Audit: Security as a Business Enabler
Security is often seen as a cost center. However, in the mortgage sector, a well-designed ZTA is a business accelerator.
Auditability and Tracking
Every transaction in a Zero Trust environment leaves a trace. Integrating tools like AWS CloudTrail or Google Cloud Audit Logs with SIEM systems allows for the exact reconstruction of who did what and when.
This level of detail drastically simplifies audits for regulations such as GDPR, PCI-DSS, and ISO 27001. Demonstrating to auditors that access to PII data is cryptographically and contextually limited reduces verification times and increases the reputation (Trustworthiness) of the financial institution.
Conclusions

Implementing a zero trust architecture for financial data on AWS and Google Cloud is not a project that ends with purchasing software, but a continuous journey of improving security posture. The integration of mTLS, contextual IAM, and BYOK encryption creates a resilient environment where the compromise of a single component does not result in catastrophic data loss.
For companies in the credit sector, investing in ZTA today means ensuring operational continuity and customer trust tomorrow, transforming compliance from a legal obligation into a competitive advantage.
Frequently Asked Questions

Zero Trust Architecture (ZTA) in the financial sector abandons the old perimeter security model to adopt the principle «Never Trust, Always Verify». Instead of implicitly trusting users inside the network, this approach requires that every single request for access to sensitive and financial data be continuously authenticated, authorized, and encrypted, ensuring superior protection against internal and external threats and PII data breaches.
In a Zero Trust model on the cloud, identity acts as the new security perimeter through granular access management (IAM) and the use of context-based policies. In addition to verifying credentials, modern systems analyze factors such as device health, geolocation, and request time in real-time; by applying the principle of least privilege, it ensures that users and services access only the resources strictly necessary for their functions.
Using the mTLS (Mutual TLS) protocol is essential to ensure that every microservice verifies the identity of the other before communicating, preventing «Man-in-the-Middle» attacks within the virtual network. Adopting a Service Mesh, such as Istio or AWS App Mesh, automates certificate rotation and encryption of traffic in transit, ensuring secure communications without having to modify the code of individual applications.
The BYOK (Bring Your Own Key) strategy allows financial institutions to maintain exclusive control over encryption keys, generating them in proprietary hardware modules instead of relying entirely on the cloud provider. This approach allows for immediate key revocation (known as «crypto-shredding»), making data instantly inaccessible in case of emergency or compromise, and ensures a clear separation of duties for regulatory compliance.
The Zero Trust approach transforms security into a business enabler by facilitating compliance with regulations such as GDPR, PCI-DSS, and ISO 27001. Thanks to detailed logging of every access and transaction via audit log tools, companies can easily demonstrate to auditors that access to sensitive data is strictly limited and monitored, reducing verification times and increasing trust in customer data management.



Did you find this article helpful? Is there another topic you'd like to see me cover?
Write it in the comments below! I take inspiration directly from your suggestions.