In Brief (TL;DR)
Recognizing a fake app on the Play Store and App Store is the first fundamental step to defending yourself against scams and malware, protecting your data and privacy.
From suspicious reviews to excessive permissions, we show you the warning signs you shouldn’t ignore.
Discover how a careful analysis of reviews, permissions, and developer details can make a difference for your security.
The devil is in the details. 👇 Keep reading to discover the critical steps and practical tips to avoid mistakes.
In the digital age, the smartphone has become an extension of our lives, a guardian of personal data, and a portal to a world of services. In this context, the applications we download from official stores like the Google Play Store and Apple App Store are the keys that open these doors. However, not all keys are safe. There is a hidden world of fake apps, created by cybercriminals with the sole purpose of deceiving users, stealing sensitive data, or generating illicit profits. Recognizing them is the first, fundamental step to defending our privacy and security, combining traditional caution with the innovation of digital awareness.
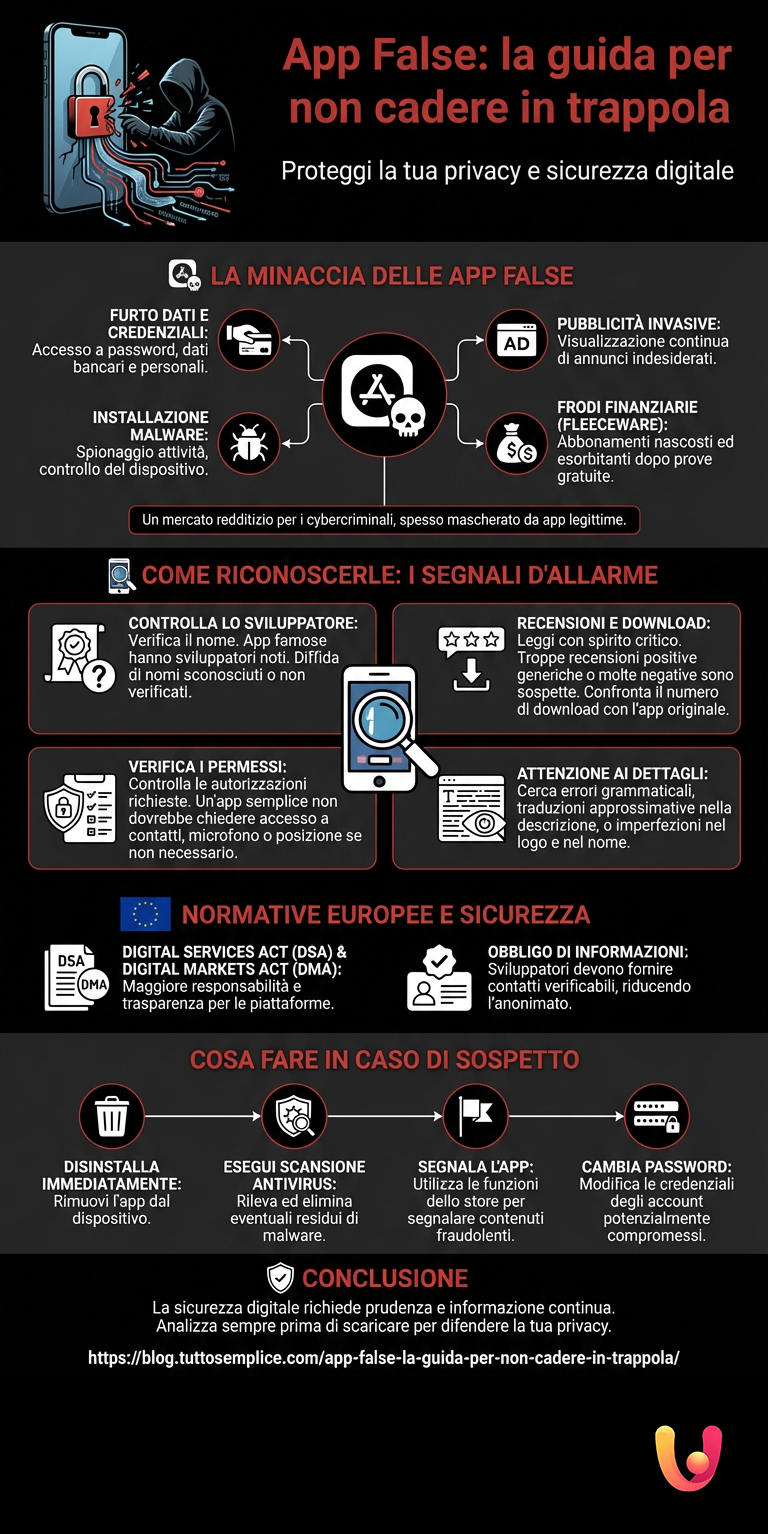
Fraudulent apps represent a significant and constantly evolving threat. They often mask themselves as legitimate and popular applications, replicating their logos and interfaces to deceive less attentive users. Once installed, they can perform a series of malicious activities: from stealing banking credentials and passwords to installing malware that spies on our activities, to displaying invasive advertisements. Understanding the tactics used by malicious actors and learning to read the warning signs is essential to navigating digital stores safely, protecting our small technological universe from unwanted intrusions.

The Fake App Market: A Concrete Threat
The phenomenon of fake apps is not a marginal risk, but a consolidated reality that generates huge profits for cybercriminals. These malicious actors register as developers on official stores, download a legitimate application, re-engineer it by inserting malicious code, and re-upload it with a slightly different name or icon. Despite the security controls implemented by Google and Apple, numerous malicious apps manage to evade surveillance nets, reaching millions of downloads before being identified and removed. This scenario is confirmed by numerous reports from cybersecurity companies, which periodically unmask malware and fleeceware campaigns.
An emblematic example is fleeceware, a category of apps that lures users with a free trial and then charges exorbitant subscription fees, sometimes exceeding 3,000 euros per year. These apps, often disguised as simple utilities like image editors or QR code scanners, rely on user inattention, as users often do not notice the charges or do not know how to cancel the subscription. According to research by Avast, over 200 apps of this type have generated more than 400 million dollars in revenue, demonstrating the vastness and profitability of this fraudulent market. The culture of prudence, typical of our traditional approach, must therefore evolve to include greater attention to the details of digital subscriptions.
How to Recognize a Fake Application: The Warning Signs
Learning to distinguish a legitimate app from a fake one is a fundamental skill for every smartphone user. There are several red flags that, if analyzed carefully, can reveal the fraudulent nature of an application before downloading. Tradition teaches us not to trust appearances, and this principle is more valid than ever in the digital world. Critical and meticulous analysis is our first line of defense against online scams.
Analyzing the App Sheet
The presentation page of an app on the store is a goldmine of information. The first element to examine is the developer’s name. Famous apps will always have the parent company’s name as the developer; if you find an unknown or suspicious name associated with a famous app, it is almost certainly a clone. Google requires developers to verify their identity, a step that adds a layer of security. Even the logo and the app name may contain small imperfections, such as typos or slight graphic alterations, designed to confuse the user. Finally, the description: texts with grammatical errors or poor translations are a strong indication of a lack of professionalism and potential bad faith.
The Power of Reviews and Downloads
Reviews from other users are a valuable tool, but they must be read with a critical spirit. An app with many negative reviews or complaints is obviously to be avoided. However, an excess of five-star reviews, perhaps brief and generic, can also be a warning sign. Scammers often use bots to generate fake reviews and artificially inflate the score. An analysis by Which? revealed that a significant percentage of the most popular apps contain suspicious reviews. Another figure to consider is the number of downloads: a very famous app will have millions of installations, while its clone will have a significantly lower number. This comparison helps to unmask the deception.
Checking Requested Permissions
Before installing an application, it is crucial to check the permissions it requires to function. If a photo editing app asks for access to your contacts or microphone, it is a clear warning sign. Fraudulent apps often request unnecessary permissions to collect as much data as possible. Both Android and iOS allow you to view and manage the permissions requested by each app. It is good practice to grant only the authorizations strictly necessary for the app’s operation and to be wary of those that demand disproportionate access, an approach that reflects healthy management of one’s personal information, just like when choosing who to trust in real life.
European Regulations and Store Security

The European regulatory context is playing an increasingly active role in strengthening user security. The Digital Services Act (DSA) and the Digital Markets Act (DMA) are two legislative pillars that impose greater responsibilities and transparency on large digital platforms, including the Apple and Google app stores. One of the most relevant novelties introduced by the DSA is the obligation for developers generating revenue to provide verifiable contact information, such as an email address and phone number, which will be visible on the app page. This increases traceability and accountability, making it harder for malicious actors to hide in anonymity.
These regulations are pushing Apple and Google to review their policies. Apple, for example, while expressing concerns about potential security risks, is adapting to allow the installation of apps from sources outside its App Store within the EU. In parallel, it is introducing new protection measures, such as the “notarization” of apps, to analyze them and block known malware. These legislative and technological evolutions represent an important step forward, combining regulatory innovation with the European tradition of consumer protection, to create a safer digital ecosystem for everyone. Choosing the first smartphone for a child, for example, becomes an act that also requires knowledge of these security dynamics.
What to Do If You Suspect You Have Installed a Fake App
If, despite precautions, you suspect you have downloaded a fraudulent application, it is essential to act quickly to limit the damage. The first, immediate, and unavoidable step is to uninstall the app from the device. Subsequently, it is advisable to run a scan with reliable antivirus software to detect and remove any malware residues the app may have left in the system. This approach combines direct action with the prevention of further problems.
After securing your device, it is important to take two further actions. The first is to report the fake app directly to the store from which it was downloaded. Both Google Play and the App Store have implemented reporting functions, recently enhanced, which allow users to flag suspicious or fraudulent content, helping to protect the entire community. The second action, if the app had access to sensitive data, is to immediately change the passwords of potentially compromised accounts (email, social networks, online banking). This step is crucial to prevent identity theft or unauthorized access. Careful management of your digital security is as important as financial management, such as when evaluating an urgent loan.
Conclusions

Security in the digital world is not a destination, but a continuous process of learning and adaptation. Recognizing fake apps on the Play Store and App Store is an essential skill that blends traditional wariness with necessary technological literacy. Carefully analyzing the developer, reading reviews with a critical eye, checking the number of downloads, and, above all, verifying requested permissions are simple but powerful gestures to defend our privacy. European regulations, such as the Digital Services Act, are introducing further protections, but the final responsibility always lies with the user.
Being conscious digital consumers means never lowering your guard, constantly updating your knowledge, and adopting a proactive approach to security. Just as we learn to recognize potentially risky situations in everyday life, we must do the same with the tools we use daily. Prudence, combined with information, remains the best antivirus against digital threats, ensuring we can fully exploit the immense opportunities offered by technology without falling into the traps of malicious actors.
Frequently Asked Questions

To recognize a fake app, check a few key elements in the store. Observe the icon and name: cloned apps often present small differences compared to the original. Read the description carefully to spot grammatical errors or unprofessional language. Analyze the reviews: an excessive number of positive and generic reviews, or conversely, many negative reviews reporting problems, are red flags. Verify the developer’s name to ensure it is the official one and check the number of downloads: a popular app will have millions of downloads, while a fake one will have significantly fewer.
Installing a malicious app exposes you to serious privacy and security risks. These apps can steal personal information such as passwords, banking data, and contacts. They can install malware, display invasive advertising (adware), or subscribe you to paid services without your consent (billing fraud). In some cases, criminals can obtain elevated privileges on the device, disabling security functions and taking control of your smartphone for illicit activities.
If you suspect you have installed a fake app, the first thing to do is uninstall it immediately from your device. Subsequently, restart your phone to stop any malicious processes running in the background. It is advisable to run a scan with reliable antivirus software to detect and remove any malware residues. Finally, report the application to the store (Google Play Store or Apple App Store) to protect other users. If you entered login data, change the passwords of the affected accounts immediately.
Checking permissions is fundamental because they define which data and phone functions the app can access. A malicious app often requests authorizations unnecessary for its operation. For example, a note-taking app should not need access to your contacts or microphone. Granting excessive permissions can allow an app to spy on you, record conversations, read your messages, or track your location. Always verifying that requested permissions are consistent with the application’s functionalities is an essential defense for your privacy.
Generally, the Android system is considered more at risk for the presence of fake apps. This is because the Google Play Store has a historically less restrictive review process compared to Apple’s App Store and allows the installation of apps from external sources (sideloading). Apple’s closed ecosystem, defined as a “walled garden”, subjects apps to stricter controls before publication, making it harder to distribute malware. However, no platform is 100% immune; fraudulent applications have occasionally been identified on the App Store as well.



Did you find this article helpful? Is there another topic you'd like to see me cover?
Write it in the comments below! I take inspiration directly from your suggestions.