Using payment cards has become a daily habit, blending the tradition of exchanging value with the modern need for fast, digital transactions. Whether it’s for a coffee at a café, the weekly grocery run, or an online purchase, the convenience is undeniable. However, this evolution has also opened the door to new threats: fraud. In a context like Italy and Europe, where Mediterranean culture intertwines with technological innovation, understanding and addressing this phenomenon is crucial to protecting our personal finances and trust in the digital system.
Cybercriminals are constantly refining their techniques to illegally steal data and money. Recognizing the signs of a scam, taking preventive measures, and knowing how to act in case of fraud are essential skills for anyone who uses a debit, credit, or prepaid card. This article offers a comprehensive guide to safely navigating the world of electronic payments, providing practical tools to defend yourself and maintain control of your finances.
The Landscape of Card Fraud in Italy and Europe
Payment card fraud is a real and constantly evolving threat. According to data from the Bank of Italy, although the incidence of fraud relative to total transactions remains low, the absolute figures are significant. In 2024, fraudulent transactions with payment cards in Italy reached 33 million euros. While this figure shows moderate growth compared to bank transfers, it highlights constant pressure on the system. Remote transactions, such as e-commerce, remain the most exposed to risk.
At the European level, the picture is no different. The Payment Services Directive (PSD2) has introduced higher security standards, such as Strong Customer Authentication (SCA), to combat fraud. However, criminals adapt, using “payer manipulation” techniques, where the victim is tricked into authorizing a payment. These scams, based on social engineering, are particularly insidious. The theft or loss of a physical card remains a significant cause of fraud, but digital threats show the most alarming growth, requiring constant vigilance from users and institutions.
The Many Faces of Scams: Types and Modus Operandi
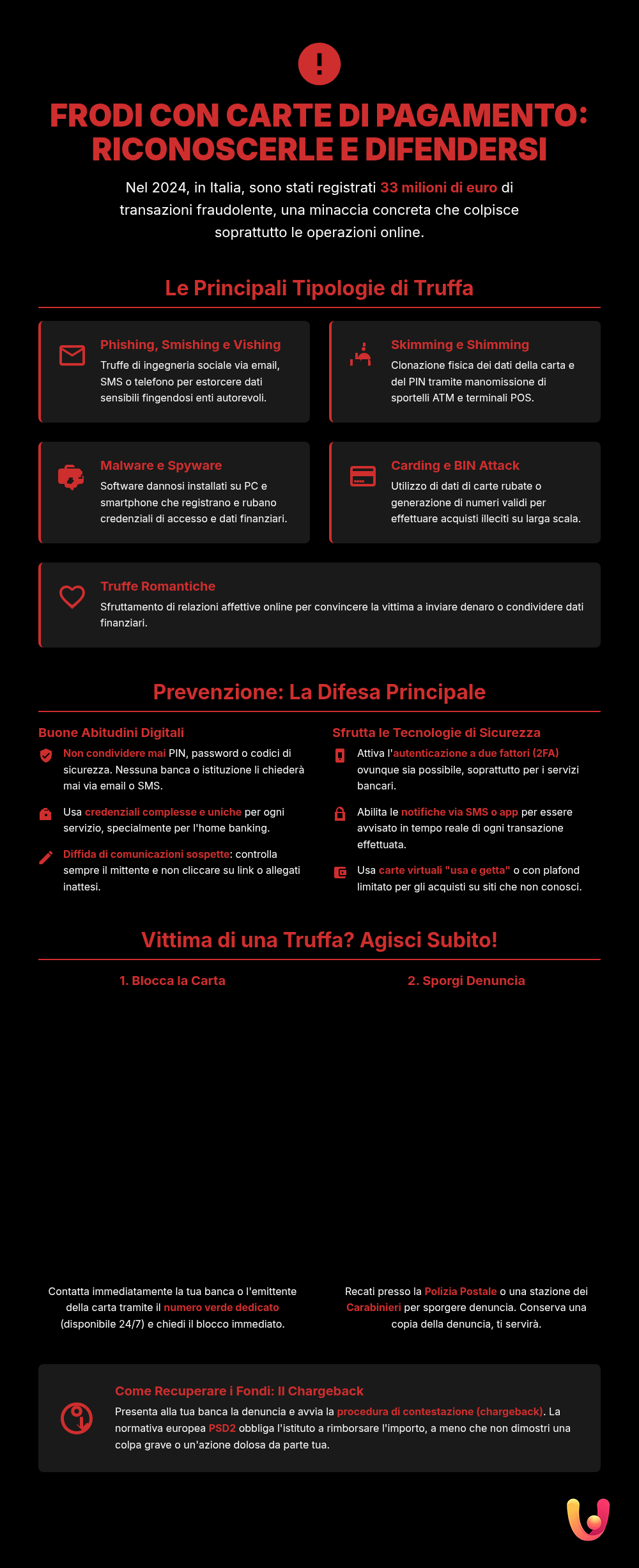
Payment card fraud comes in many forms, each with its own specific *modus operandi*. Criminals exploit both technology and human psychology to achieve their goals. Knowing the main types of scams is the first step to learning how to effectively defend yourself and protect your savings. From deceptive emails and fraudulent phone calls to the physical tampering of devices, every technique has a single purpose: to obtain your card details.
Phishing and Smishing: The Digital Bait
Phishing is one of the most common scams and relies on sending emails that appear to come from trusted sources, such as banks, couriers, or well-known online services. These messages, often with an alarming tone, push the victim to click a link that leads to a cloned website. Once on the fake site, the user is prompted to enter their personal data and card credentials, handing them directly to the scammers. Smishing is the variant that uses SMS messages as the attack vector. A text message on your phone, notifying you of a supposed problem with your account or a package delivery, invites you to click a malicious link with the same goal as phishing. To protect yourself, it’s essential to learn how to recognize these phishing and smishing attempts.
Vishing: The Scam on the Other End of the Line
Vishing, a term born from the fusion of “voice” and “phishing,” is a scam conducted over the phone. Criminals pose as bank employees, law enforcement officers, or credit card company representatives. They contact the victim to report alleged suspicious activity on their account or card. Using clever psychological manipulation techniques, they convince the victim to reveal sensitive data like passwords, PINs, or card numbers, or to authorize transactions that are actually fraudulent. Scammers often already have some basic information about the victim, making the call even more believable. Never trust anyone who asks for confidential data over the phone: your bank will never ask for it this way. This type of scam is known as vishing, or the phone scam.
Skimming and Shimming: The Physical Theft of Data
Skimming is a fraud technique that involves physically tampering with ATMs or point-of-sale (POS) terminals. Criminals install a device, the *skimmer*, over the card slot to copy data from the magnetic stripe. At the same time, a hidden micro-camera or an overlay keypad records the PIN entered by the user. Shimming is a more advanced version that targets chip cards by inserting a wafer-thin device, the *shimmer*, into the card reader to intercept data. To protect yourself, it’s good practice to always check that the terminal shows no signs of tampering or loose parts before inserting your card and to always cover the keypad with your hand while entering your PIN. For more details on how to protect yourself, it’s helpful to consult the guide on how to recognize a tampered ATM.
Malware and Spyware: The Invisible Enemy
Malware and spyware are malicious software installed on a computer or smartphone without the user’s knowledge. Infection can occur by clicking on links or attachments in phishing emails, downloading apps from unofficial sources, or browsing compromised websites. Once active, malware can have various functions: spyware, for example, can monitor everything you do, recording your home banking login credentials or the credit card details you enter during online purchases. *Keyloggers*, a specific type of spyware, record every keystroke. These invisible tools operate in the background, stealing valuable information without the victim noticing until it’s too late.
Carding and BIN Attacks: The Assault on Numbers
Carding is the criminal activity of using stolen credit card data to make fraudulent purchases. Scammers test the validity of the data by making small transactions before moving on to larger amounts. A related technique is the BIN attack, a type of brute-force attack where criminals use software to generate thousands of possible credit card numbers starting from a known “Bank Identification Number” (BIN), which are the first 6-8 digits that identify the issuing institution. Once they find a valid card number, they try to guess the expiration date and CVV to use it. These techniques are often automated by bots and pose a significant threat to the online payment ecosystem. To better understand these threats, you can learn more about Carding and BIN Attack techniques.
Emotional Scams: When the Heart is the Target
Romance scams exploit people’s feelings and emotional vulnerabilities. Scammers create fake profiles on dating sites or social media, building a long-distance relationship with the victim. After establishing a bond of trust, which can take weeks or months, they invent complicated and urgent stories: a sudden medical emergency, a work problem abroad, or the need for money to finally meet the victim. At this point, they ask for money to be sent via wire transfer or for credit card details to be shared. This form of scam not only causes financial damage but also leaves deep emotional wounds, exploiting trust and the desire for affection.
Prevention: The First Line of Defense
The best defense against fraud is *prevention*. Taking a proactive and conscious approach to managing your payment cards and personal data drastically reduces the risk of falling victim to criminals. It’s not about living in fear, but about integrating a few simple yet crucial habits into our daily and digital routines. The security of our money largely depends on us, our attention, and our knowledge of the technologies available to protect ourselves.
Protecting Data with Good Digital Habits
Protecting your personal data is the first shield against fraud. It is crucial never to share sensitive information such as PINs, passwords, or security codes via email, SMS, or phone. No legitimate bank or institution will ever request this data in such a way. Use complex and unique passwords for each online service, especially for home banking and e-commerce sites. Always be wary of unexpected emails and messages that demand urgent action: always verify the sender and do not click on suspicious links. Finally, be careful about what you share on social media, as scammers can use this information to build personalized attacks.
Technologies on Our Side: How to Use Them Best
Technology offers powerful tools to increase payment security. Always enable two-factor authentication (2FA), which requires a second verification code (usually sent to your smartphone) to authorize logins or transactions. Use the SMS or app notification services your bank offers to be alerted in real-time of every transaction made with your card. For online purchases, consider using disposable virtual cards or cards with a limited spending cap, which reduce the risk in case of a data breach on the e-commerce site. Finally, always keep the operating system and antivirus software on your devices updated to protect yourself from malware and spyware.
What to Do Immediately If You Are a Victim of Fraud
Realizing you’ve been a victim of payment card fraud can cause anxiety and confusion. However, acting quickly and methodically is crucial to limit the damage and start the process of recovering your money. There are specific steps to follow that allow you to secure your accounts and assert your rights. Timeliness is the most important factor: every minute lost could allow scammers to carry out further illicit transactions.
Blocking the Card and Filing a Report: The First Crucial Steps
The very first action to take as soon as you suspect or confirm fraud is to immediately contact your bank or card issuer to have the card blocked. Every financial institution provides a dedicated toll-free number, available 24/7, for these emergencies. Blocking the card will prevent any further unauthorized use. Immediately after, you must go to law enforcement (such as your local police) to file a report. A copy of the report is an essential document that must be attached to the refund request submitted to the bank.
The Refund: How and When to Request It
Once the card is blocked and a report has been filed, you must start the dispute process for the unauthorized transactions, also known as a *chargeback*. You will need to fill out a dispute form provided by your bank, attaching the police report. According to the European PSD2 directive, adopted in Italy, in the case of an unauthorized transaction, the bank is required to immediately refund the stolen amount, at the latest by the end of the business day following the notification. The bank can only refuse the refund if it can prove that the customer acted with fraudulent intent or gross negligence, for example, by keeping the PIN with the card or sharing credentials with third parties. The deadline for disputing a transaction is 13 months from the date of the charge.
In Brief (TL;DR)
From common scams like phishing to more sophisticated techniques, this comprehensive guide gives you all the tools to recognize, prevent, and effectively defend yourself against payment card fraud.
We will explore the scammers’ modus operandi and provide you with a practical guide on countermeasures to protect your savings.
Finally, find out what to do and who to turn to if you are a victim of fraud to protect your account and recover your funds.
Conclusion

Payment card fraud is a complex phenomenon that combines criminal tradition with technological innovation. In a context like Italy’s, deeply rooted in its habits but projected towards the digital world, awareness is the keystone. Protecting yourself doesn’t mean giving up the convenience of electronic payments, but learning to use them intelligently and prudently. Recognizing scammers’ techniques, from phishing to skimming, adopting good security practices like using strong passwords and two-factor authentication, and knowing how to react promptly in case of fraud are the most effective weapons at our disposal. The collaboration between users, banking institutions, and law enforcement, combined with European regulations that protect consumers, creates a safer ecosystem for everyone, allowing us to embrace the future of payments without fear.
Frequently Asked Questions

If you notice a charge you don’t recognize, the first and most important action is to block your card immediately. You can do this through your bank’s app, online banking service, or by calling the dedicated toll-free number, which is active 24/7. Immediately after, contact your bank to dispute the transaction and start the refund process. Finally, file a report with the relevant authorities, such as the local police, to formalize the incident.
You can recognize a phishing email by paying attention to a few signs. Always check the sender’s address, which often looks legitimate but may contain slight errors or come from a generic domain. Be wary of alarming tones that urge you to act quickly, such as the threat of blocking your account. Don’t click on suspicious links; hover your mouse over them to see the real URL. Finally, remember that your bank will never ask you to provide passwords, PINs, or sensitive data via email.
Yes, contactless payments are considered very secure. Each transaction uses advanced encryption to protect card data. Additionally, for amounts above a certain threshold (usually €50 in Europe), extra authentication is required, such as entering a PIN or unlocking with biometric recognition on a smartphone. The NFC (Near-Field Communication) technology only works at a very close range, making it extremely difficult for malicious actors to intercept the data.
Generally, yes. The European PSD2 directive, adopted in Italy, requires banks to refund customers for unauthorized transactions. The financial institution is obliged to return the amount unless it can prove that the customer acted with fraudulent intent or ‘gross negligence,’ for example, by keeping their PIN with their card or voluntarily sharing their credentials with third parties. For fraudulent transactions that occurred before the card was blocked, a maximum liability of €50 may be applied to the customer.
Saving your card details can be convenient, but it increases the risks in the event of a cyberattack on the merchant’s site. For greater security, it is advisable to use this feature only on sites with proven reliability that use the HTTPS protocol. A valid alternative is to use digital wallets like PayPal, Apple Pay, or Google Pay, which do not directly share your card details with the seller. Another excellent strategy is to use ‘single-use’ virtual cards provided by many banks, which generate a card number valid for a single transaction.
Still have doubts about Card Fraud: A Guide to Recognizing It and Taking Action?
Type your specific question here to instantly find the official reply from Google.







Did you find this article helpful? Is there another topic you’d like to see me cover?
Write it in the comments below! I take inspiration directly from your suggestions.