Contactless payments have become a daily routine for millions of Italians. Tapping a card, smartphone, or smartwatch on the POS is a habit that combines speed and convenience, accounting for nearly 90% of in-store electronic transactions. This epochal shift, accelerated in recent years, saw digital payments surpass cash in Italy for the first time in 2024, with a value of 481 billion euros. But as technology advances, a central question remains for many consumers: what data is transmitted during a “tap & go” transaction? And, above all, is our privacy truly protected? In a country like Italy, where the tradition of cash confronts an increasingly strong push towards innovation, it is fundamental to clarify matters.
Unfortunately, growing familiarity with these tools often clashes with doubts and fears regarding security. Stories of hi-tech theft and the fear that sensitive data might be intercepted fuel a certain mistrust. Yet, the technology behind contactless payments is designed precisely to be secure. Understanding which information is exchanged and which remains protected is the first step to using these tools with full awareness, combining the practicality of innovation with the peace of mind of a secure transaction.
How a Contactless Payment Works
At the heart of every contactless payment is a short-range communication technology called NFC (Near Field Communication). It is an evolution of the better-known RFID (Radio Frequency Identification) that allows two devices, such as a payment card and a POS terminal, to exchange data securely when they are at a minimum distance, usually no more than 4 centimeters. This extremely short range is the first, fundamental security barrier: it prevents accidental or remote interception. When you bring the card or smartphone close to the reader, the NFC chip “activates” and initiates an encrypted communication with the terminal to complete the purchase in moments. To learn more about this fascinating technology, you can read our guide on how NFC works.
What Data Is Actually Transmitted
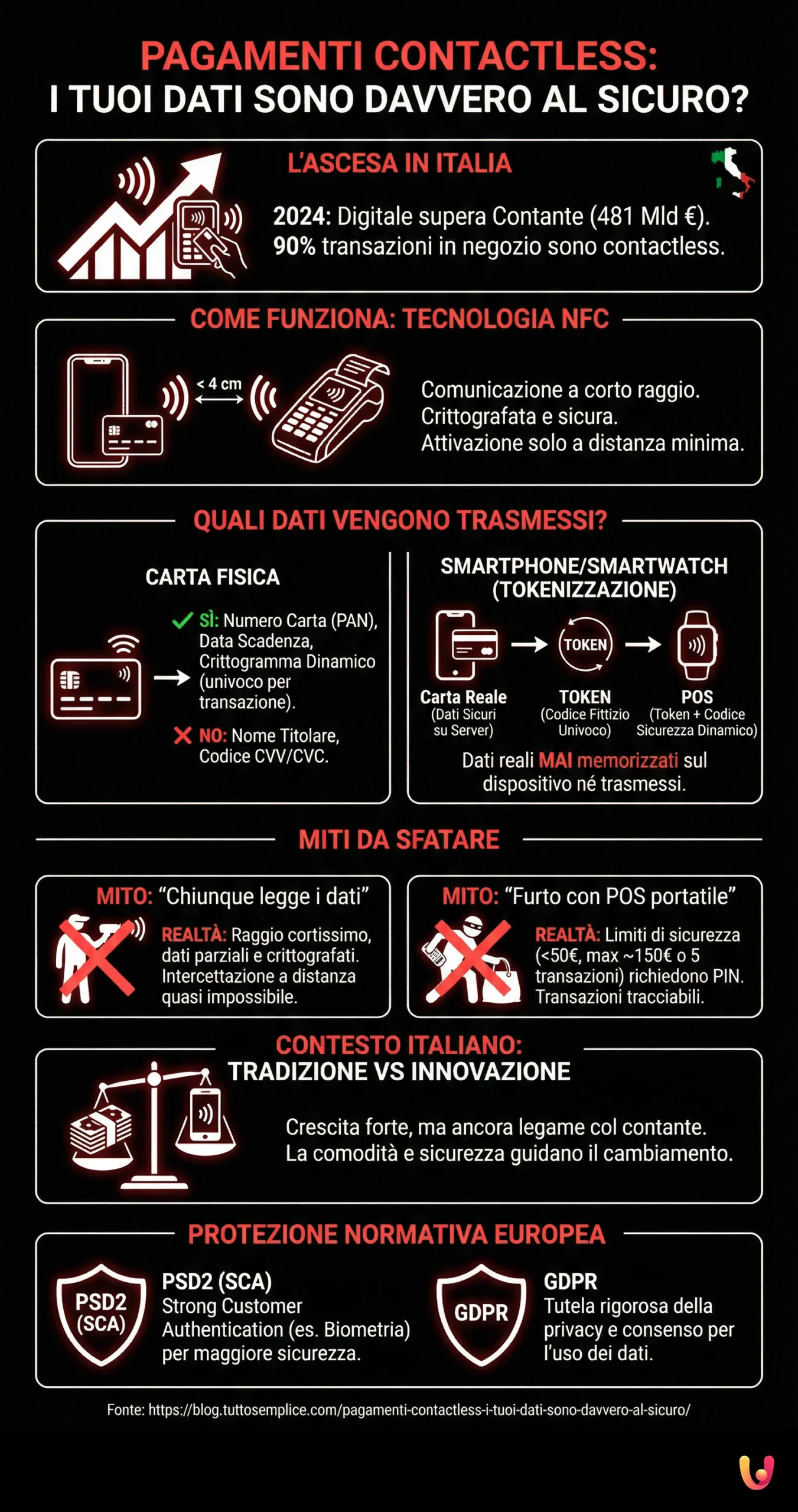
The main concern regarding contactless payments regards the nature of the data exchanged. It is a legitimate fear, but based on an often incorrect idea of what happens during the transaction. The system’s security is founded precisely on the principle of data minimization: only what is strictly necessary to authorize the payment is shared, protecting information that uniquely identifies the holder. Let’s analyze in detail what happens with different payment tools.
Data Exchanged by the Physical Card
When using a physical credit or debit card for a contactless payment, the information transmitted from the NFC chip to the POS is essentially twofold: the card number (PAN) and its expiration date. However, this data does not travel “in the clear”. It is sent through an encrypted channel and, above all, is accompanied by a dynamic code (a cryptogram) that changes with every single transaction. This code serves to certify that the card is authentic and that the transaction is unique. Personal information like the cardholder’s first and last name or the 3-digit CVV/CVC code on the back is never transmitted. This makes the data, even if hypothetically intercepted, effectively unusable for making new fraudulent transactions, especially online, where the CVV is almost always required.
The Added Security of Smartphones and Smartwatches: Tokenization
When paying with a smartphone or smartwatch via services like Apple Pay or Google Pay, the security level increases further thanks to a process called tokenization. In this case, the real card data is never stored on the device nor transmitted to the merchant’s payment terminal. At the time of digital wallet configuration, a “token” is associated with the card, which is a unique and fictitious numeric code. During payment, it is this token, and not the real card number, that is sent to the POS, always accompanied by a security code valid for that single operation. This system offers double protection: the original card data remains safe on the bank’s secure servers, and in case of phone theft or loss, no one will be able to access the real information. For a complete overview, discover our guide on secure payments with tokenization and biometrics.
Myths to Debunk About Contactless Privacy

Despite robust security measures, contactless payments are still surrounded by false myths that generate unjustified anxiety. It is important to analyze the most common concerns and understand why, in most cases, they are unfounded. The reality is that, although no system is 100% infallible, contactless is designed to be one of the safest payment methods available to us.
“Anyone can read my personal data from the card”
This is one of the most widespread but technically unfounded fears. As we have seen, transmitted data is limited and does not include identifying personal information like the name. Furthermore, NFC technology requires a proximity of a few centimeters to function, making “remote” interception without the owner’s knowledge extremely difficult. A malicious actor would have to be physically attached to the victim with a specialized reader, a complex and risky operation. Even in this unlikely scenario, the obtained data would be encrypted and lacking the CVV, rendering it almost useless for fraud.
“Thieves can empty my account with a portable POS”
The image of a thief brushing against a bag with a POS has become a classic of media fear-mongering regarding contactless. Although cases exist in the news, it is a much more limited risk than one might think. For transactions under 50 euros, a PIN is not required, but payment circuits impose security limits: after a certain number of consecutive operations (usually 5) or upon reaching a cumulative amount (around 150 euros), the system mandatorily requests PIN entry to verify the holder’s identity. This mechanism prevents large-scale fraudulent withdrawals. Furthermore, every POS is linked to a bank account and a registered merchant, making transactions traceable and scams difficult to execute without being discovered. In case of contactless fraud, regulations extensively protect consumers.
The Balance Between Tradition and Innovation in Italy
The Italian context offers an interesting cross-section of the relationship between established habits and new technologies. Italy, while showing double-digit growth in the adoption of digital payments, still remains in 24th place out of 27 in Europe for the number of per capita card transactions. This figure reflects a culture where cash has always played a central role, not only out of habit but also due to perceived greater privacy and control over spending. However, the convenience and speed of contactless are winning over more and more Italians. In 2024, for the first time, the value of digital transactions surpassed that of cash. This historic overtaking, driven precisely by “tap & go”, demonstrates that even in a traditionally cautious market, innovation, when practical and secure, manages to make its way and profoundly change daily habits.
The Regulatory Context: GDPR and PSD2 Protection
Trust in digital payments relies not only on technology but also on a solid European regulatory framework. The Payment Services Directive (PSD2) introduced higher security standards, such as Strong Customer Authentication (SCA), which requires at least two authentication factors (something you know, like a PIN; something you have, like a smartphone; or something you are, like a fingerprint) for most electronic transactions, increasing protection against fraud. Parallel to this, the General Data Protection Regulation (GDPR) imposes strict rules on how companies can collect, process, and protect users’ personal data. Any data processing going beyond simple payment execution, such as for marketing or profiling purposes, requires explicit and informed consent from the user. These regulations create an ecosystem where the consumer is protected both from the standpoint of transaction security and the privacy of their personal information.
In Brief (TL;DR)
Discover which data is really transmitted during a contactless payment and why your sensitive information, like the cardholder’s name and CVV, remains safe.
We analyze which data is effectively shared during a contactless transaction and why the most sensitive information, such as the cardholder’s name or CVV, is not transmitted.
Only data essential for the operation is exchanged, protecting the most sensitive information thanks to technologies like encryption and tokenization.
Conclusions

Contactless payments represent one of the most convenient and successful innovations of recent years, capable of simplifying our daily lives. Privacy concerns, while understandable, are largely mitigated by advanced technologies like encryption and tokenization, which ensure a high level of security. Transmitted data is reduced to the bare minimum and protected to prevent fraudulent use. The European regulatory framework, with PSD2 and GDPR, adds an extra layer of protection, holding operators accountable and protecting consumer rights. In an Italy traveling halfway between tradition and a digital future, understanding how these tools work is essential to enjoying their benefits with peace of mind. Contactless is not only fast but also secure: a valuable ally in an increasingly digital world.
Frequently Asked Questions

During a contactless payment, only data essential for the transaction is transmitted: the card number (often in the form of a temporary code called «token») and the expiration date. Sensitive data like the cardholder’s name, the 3-digit CVV code, or the PIN are never transmitted. This makes the transaction secure and protects your privacy.
Although technically possible, this scenario is extremely unlikely and rare. NFC technology requires a minimum distance of a few centimeters between the card and the reader. Furthermore, every transaction generates a «disposable» code, and the POS terminal must be registered to a merchant, making the fraudster easily traceable. Using digital wallets like Apple Pay or Google Pay further increases security, as the real card number is never shared.
Yes, payments via smartphone (like Google Pay or Apple Pay) are generally considered more secure. This is because they use a process called «tokenization», which replaces your real card number with a unique digital code for every transaction. Plus, they almost always require authentication via PIN, fingerprint, or facial recognition, adding an extra layer of protection that the physical card does not have for small amounts.
No, they cannot empty your account. In Italy and Europe, there is a 50€ limit for single contactless transactions made without entering the PIN. Additionally, there is a cumulative limit (usually 150€) or a maximum number of consecutive operations (usually 5), after which the PIN is mandatorily required. In case of theft or loss, it is crucial to block the card immediately by contacting your bank.
Security is based on multiple levels. First, NFC technology works only at very close range (a few centimeters). Second, transmitted data is encrypted, and a dynamic code valid for only one transaction is generated. Third, for amounts over 50€, PIN or biometric authentication is always required. Finally, systems like the tokenization used by smartphones hide the true card number, offering even greater protection.
Still have doubts about Contactless Payments: Is Your Data Really Safe??
Type your specific question here to instantly find the official reply from Google.








Did you find this article helpful? Is there another topic you’d like to see me cover?
Write it in the comments below! I take inspiration directly from your suggestions.