Contactless payments have become a staple of daily life, a quick and almost automatic gesture at the coffee shop, the supermarket, or on public transportation. In Italy, a country with a strong cash-based tradition, the adoption of these technologies has marked a true cultural revolution, further accelerated by the need to reduce physical contact during the pandemic. Today, nearly nine out of ten in-store payments are made contactlessly, a figure that attests to a profound change in consumer habits. This transition toward a cashless society, however, raises questions about security: is our money really safe when we pay with a simple “tap”?
The spread of digital payments, which in Italy surpassed cash for the first time in 2024, brings with it a mix of perceptions, often dominated by myths and unfounded fears. It is therefore essential to clarify the facts. Analyzing how the technology works, what the real—albeit limited—risks are, and, above all, what precautions to take, allows us to use cards, smartphones, and smartwatches with greater awareness. This article aims to debunk the most common urban legends and provide a practical guide to navigating the world of contactless payments safely, balancing innovation and tradition.
How Contactless Payments Work
At the core of contactless payments is a technology called NFC (Near Field Communication), an evolution of the better-known RFID (Radio Frequency Identification). NFC allows two devices, such as a payment card and a POS terminal, to exchange data wirelessly, provided they are at a very close distance, usually less than 4 centimeters. This extremely short range is the first, fundamental security measure: it prevents unintentional transactions or remote interceptions. When the card or smartphone is brought near the reader, the NFC chip activates and transmits the necessary information to complete the purchase in seconds.
Transaction security is ensured by multiple layers of protection. The first is encryption: payment data is converted into an unreadable code for anyone without the key to decrypt it. Additionally, for payments via smartphone and smartwatch, tokenization comes into play. This process replaces the actual card data with a “token,” a unique and temporary numerical code valid only for that specific transaction. This way, the card number is never stored on the device or transmitted to the merchant, offering a higher level of security than the physical card. Finally, authentication via PIN or biometric data (fingerprint or facial recognition) adds another shield against fraud.
Myths About Contactless Security
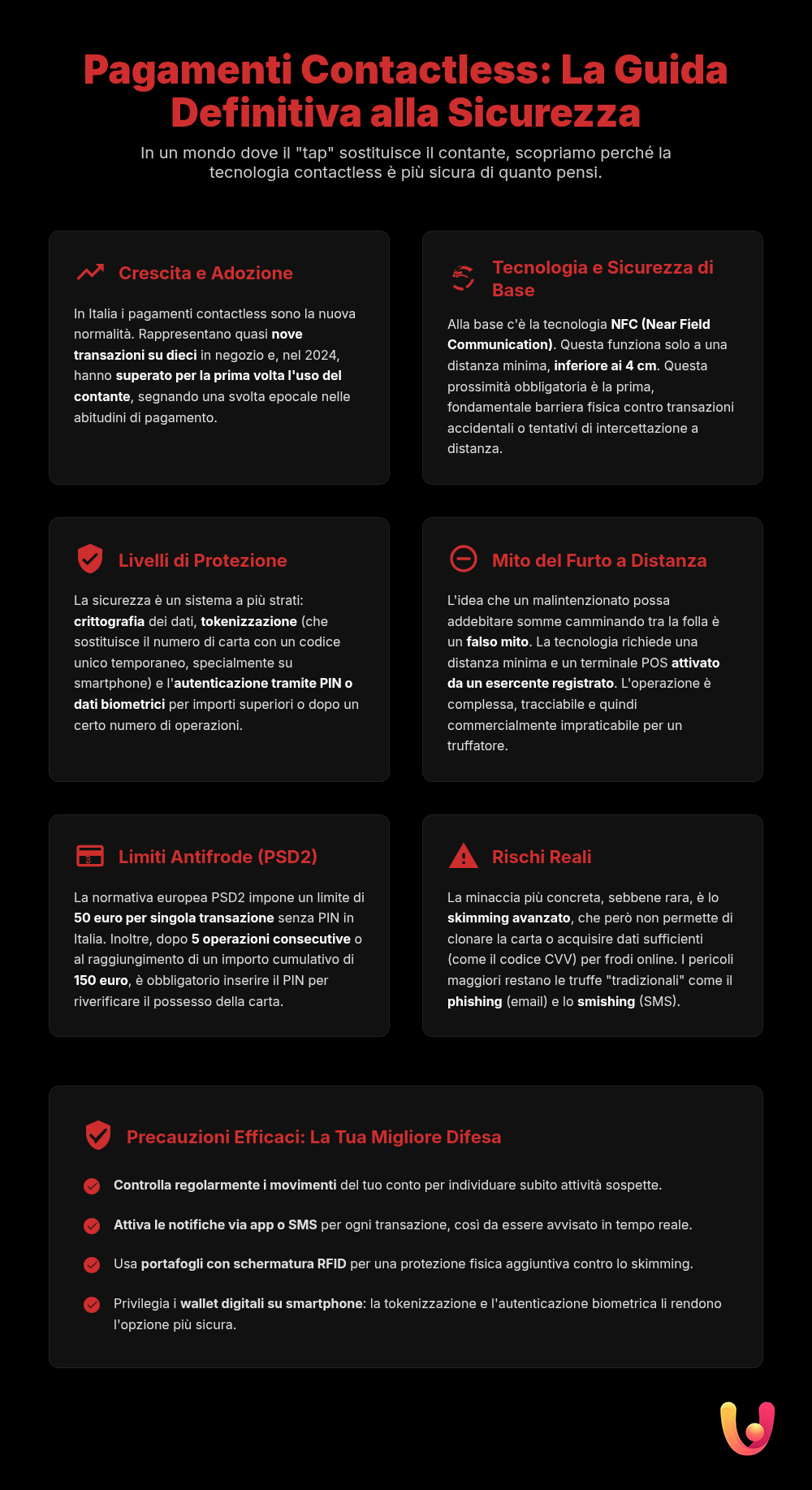
One of the most common fears is having money stolen simply by walking through a crowd. The idea that a malicious person, armed with a portable POS terminal, could “drain” your account by getting close to your bag or pocket is a classic example of misinformation. The reality is quite different. To initiate a transaction, a registered merchant must activate their terminal for a specific operation. Furthermore, the distance required for NFC communication is so short (a few centimeters) that such an attempt is extremely unlikely in a crowded environment.
Another myth to debunk concerns the ability to make multiple, unlimited payments with a stolen card. The European PSD2 (Payment Services Directive 2) regulation has introduced strict security measures. In Italy, the limit for a single contactless transaction without a PIN is €50. Above this threshold, authentication is required. Additionally, after a certain number of consecutive transactions (usually five) or upon reaching a cumulative amount (set at €150), the system mandatorily requires the PIN to be entered to verify that the card is still in the possession of its rightful owner. These limits make it very difficult for a thief to commit significant fraud.
The Real Risks and How to Protect Yourself
Although contactless payments are structurally secure, no system is 100% immune to risks. The most concrete threat, however rare, is related to advanced skimming techniques. A malicious individual could, in theory, use a boosted RFID reader to intercept data transmitted from the card at a very short distance. However, the information obtainable this way (usually the card number and expiration date) is not sufficient to make complex online transactions, which require the CVV code, or to physically clone the card’s chip. The real danger, rather than from contactless itself, comes from established scam practices like phishing and smishing, which aim to steal credentials through deception.
The first line of defense is awareness. It is good practice to regularly check your bank account statements to promptly identify any suspicious charges. Activating app notifications for every transaction is an effective tool for real-time monitoring. In case of a stolen or lost card, it is crucial to block it immediately by contacting your bank. For those who want additional protection, there are shielded wallets with RFID-blocking technology, which create a sort of “Faraday cage” to prevent unauthorized readings. Finally, using digital wallets on smartphones and smartwatches increases security, thanks to tokenization and biometric authentication, making mobile payments even more secure.
Practical Precautions for Daily Use
Safely integrating contactless payments into your daily routine requires a few, but important, habits. When paying, it’s always a good idea to check the amount displayed on the POS terminal before tapping your card or phone. Avoiding keeping cards in external or easily accessible pockets can reduce the risk of traditional theft and skimming attempts in very crowded places. If you use your smartphone to pay, it is essential to protect it with a strong PIN, a complex unlock pattern, or, even better, with your fingerprint or facial recognition. These security systems prevent access to the digital wallet even if the device is stolen.
In Brief (TL;DR)
Despite their growing popularity, contactless payments are still surrounded by security myths: let’s discover the real risks and how to protect yourself effectively.
Let’s clarify the facts by distinguishing between the myths about remote data theft and the real precautions to take for complete security.
Finally, we will explore the real, albeit limited, attack vectors and the effective precautions to mitigate them, such as using RFID-shielded wallets.
Conclusions

Contactless payments represent a technological innovation that has successfully combined convenience and security, finding fertile ground even in a culture, like the Mediterranean one, historically tied to the tradition of cash. The exponential growth of their use in Italy demonstrates a shift in mindset and an openness to solutions that simplify daily life. Fears related to “remote” data theft are largely fueled by myths and misinformation, while protection systems like encryption, tokenization, and the limits imposed by the PSD2 regulation offer a solid shield against fraud. The real risks, although they exist, are limited and can be further mitigated with simple yet effective precautions. Adopting good habits, such as periodically checking transactions and using your devices consciously, is the key to fully enjoying the convenience of contactless without undue anxiety. True security, in fact, lies in a balance between advanced technology and an informed, attentive consumer.
Frequently Asked Questions

This is a common myth, but it’s extremely unlikely in reality. The NFC (Near Field Communication) technology used for contactless payments only works over a very short distance, usually less than 4-5 centimeters. A thief would have to be almost in physical contact with your card. Furthermore, the transaction would be limited to €50 (in Italy), it would be traceable, and even if it succeeded, banks offer protections and refunds for unauthorized transactions.
In Italy and much of Europe, the limit for a single contactless transaction without entering a PIN is €50. However, for security reasons imposed by the European PSD2 regulation, after a certain number of consecutive transactions (usually 5) or upon reaching a cumulative amount (often €150), the system will still require you to enter your PIN to verify your identity.
It’s very difficult. During a contactless transaction, not all the data needed for an online purchase is transmitted. Specifically, the 3 or 4-digit security code (CVV or CVC) on the back of the card is never communicated. Without this code, most e-commerce sites will block the transaction. Additionally, many cards use “tokenization,” replacing the real card number with a one-time-use code, making any intercepted data useless.
Yes, RFID-shielded wallets and sleeves are effective. They contain a thin layer of material, like aluminum, that blocks radio waves, preventing any unauthorized external reader from communicating with your card’s chip. Although the risk of remote theft is low, using a shielded wallet is a simple, low-cost precaution for added protection and peace of mind.
The first thing to do is immediately contact your bank or card issuer to block it and prevent further fraud. Next, you must dispute the transaction by filing a formal claim. Under the regulations, you are entitled to a refund for the stolen funds, unless the bank can prove gross negligence on your part. It is also advisable to file a report with law enforcement.
Still have doubts about Contactless Payments: The Real Risks and the Myths to Debunk?
Type your specific question here to instantly find the official reply from Google.







Did you find this article helpful? Is there another topic you’d like to see me cover?
Write it in the comments below! I take inspiration directly from your suggestions.