Imagine being on a crowded bus or in a packed square. A thought crosses your mind: could a malicious person have a portable POS and, simply by bringing it close to your pocket or purse, steal money from your contactless card? This concern, fueled by sporadic news and word of mouth, has become common in the era of digital payments. In an Italy where the tradition of cash clashes and blends with the innovation of “tap and go” payments, it is legitimate to ask how safe our cards are. The short answer is that this type of theft, while technically conceivable, is in practice extremely unlikely and not very advantageous for a criminal. There are multiple layers of security, both technological and procedural, that make this scenario more of an urban legend than a concrete risk.
In this article, we will analyze in detail how contactless technology works, the integrated security barriers, and the practical reasons why criminals prefer other avenues. We will discover why, despite appearances, paying with your contactless card remains one of the safest transaction methods at your disposal, combining modern convenience with the peace of mind needed in everyday life.
How Contactless Technology Works
At the heart of contactless payments is NFC (Near Field Communication) technology, an evolution of the better-known RFID (Radio-Frequency Identification). This technology allows two devices, such as your card and a POS terminal, to communicate wirelessly when they are at a very close distance, usually no more than 1.5-2 inches (3-4 centimeters). This physical proximity represents the first, fundamental barrier against unwanted access. A thief could not charge you from a distance but would have to be physically attached to you, making the operation visible and risky.
During the transaction, the exchanged data is not transmitted in plain text. Advanced encryption systems are used that transform sensitive information into a code unreadable to anyone without the correct decryption key. Furthermore, a unique code is generated for each purchase, valid for that single operation. This process, known as tokenization, ensures that your real card number is never shared with the merchant or transmitted over the air, making intercepted data completely useless for future transactions.
Spending Limits as the First Security Barrier
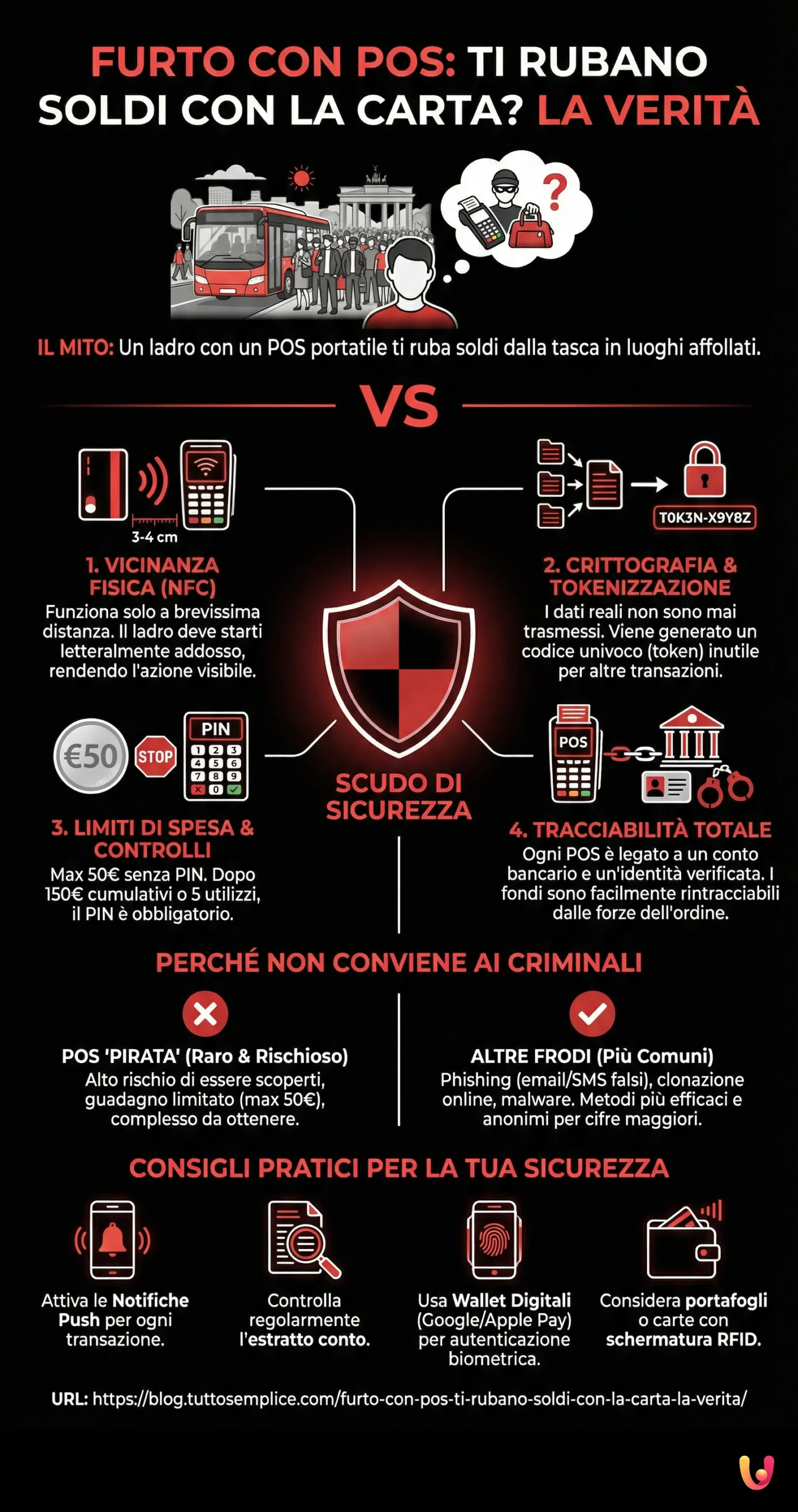
A crucial element for the security of contactless payments is the spending limit for transactions that do not require entering a PIN. In Italy, as in much of Europe, this threshold has been set at 50 euros. This means that any theft attempt via a “pirate” POS could not exceed this amount per single operation. A thief would therefore have to make multiple transactions to accumulate a significant sum, an action that would exponentially increase the risk of being discovered.
Furthermore, the European PSD2 regulation has introduced additional controls to ensure that the person using the card is the legitimate owner. After a certain number of consecutive operations without a PIN (usually five) or upon reaching a cumulative amount (set at 150 euros), the system will mandatorily require the entry of the security code. These limits were designed precisely to minimize losses in case of theft or loss of the card and make “pickpocketing 2.0” a decidedly unprofitable activity.
Why a Thief Wouldn’t Use a POS

Beyond technological barriers, there are extremely practical reasons that make POS theft an illogical choice for a criminal. The main one is traceability. Obtaining a POS terminal is not like buying just any object; it requires signing a contract with a bank or a payment service provider. This contract is always linked to a specific identity and a business bank account (merchant account), where the stolen funds would be credited. Every single transaction is recorded, tracked, and easily traceable to the account holder. For law enforcement, tracing the culprit would therefore be a relatively simple operation.
Another deterrent is the complexity and costs of the operation. Opening a business account and obtaining a POS involves identity verification procedures and management costs. It is a significant effort for a criminal activity with uncertain gain limited to 50 euros at a time. Cybercriminals, unfortunately, have much more effective and anonymous methods available to steal money, such as phishing (fake emails or SMS), card cloning via traditional skimmers, or spreading malware. These techniques allow them to obtain sensitive data and access much larger sums, with a decidedly lower risk of being discovered.
Tokenization: The Heart of Digital Security
To fully understand the security of modern payments, it is essential to focus on tokenization. Imagine entering a casino: you don’t play with your money, but with chips that represent it. These chips have value only inside the casino and cannot be used elsewhere. Tokenization works similarly: when you pay contactless, your card number (PAN) is not sent to the POS. Instead, a “token” is generated, which is a random sequence of numbers, valid only for that specific transaction.
This token is transmitted in encrypted form to the payment network (such as Visa or Mastercard), which is the only one able to decrypt it and link it to your real account to authorize the charge. Even if a malicious person managed to intercept this token, they would end up with a useless code, as it could not be reused for other purchases. This mechanism is the basis of security not only for physical cards but also for digital wallets like Google Pay and Apple Pay, which add an additional layer of protection via biometric authentication.
Myths to Debunk and the Reality of Facts
It is time to address the most common doubts directly. The main myth is that of the “thief emptying the account with a POS.” The reality, as we have seen, is quite different. Due to the 50-euro limit per operation and cumulative checks, emptying an account is impossible. Furthermore, multiple and close transactions from a single POS to the same card would immediately trigger the banks’ anti-fraud alarm systems, which would block both the card and the terminal. The rare news reports mentioning this type of scam are often isolated and linked to specific contexts, but they do not represent a widespread phenomenon.
Another myth is that card data is vulnerable during transmission. The reality is that the combination of encryption and tokenization makes the data unreadable and unusable even if intercepted. Official statistics on payment card fraud, such as those periodically published by the Bank of Italy or the MEF, show that the incidence of fraud on in-store payments (Card Present) is very low. The vast majority of fraud occurs “remotely” (Card Not Present), typically online, following scams such as phishing, where the victim themselves unknowingly provides their data.
How to Protect Yourself Further: Practical Tips
Although the risk of theft via POS is minimal, adopting good habits contributes to greater peace of mind. The first rule is to regularly check your card statement. This allows you to quickly identify any unauthorized charges and dispute them promptly with your bank. In case of suspicious transactions, it is crucial to contact the credit institution immediately to block the card.
Another powerful tool is push notifications. Almost all banking apps allow you to activate real-time alerts for every transaction made. Receiving an immediate notification for a payment you did not authorize allows you to act instantly. For those who want a physical level of protection, RFID-shielded wallets or special “shielding cards” to insert in the wallet are available on the market, which block the NFC signal and prevent any unwanted communication. Finally, using wallets on smartphones or smartwatches offers additional security, as every payment, even under 50 euros, requires authentication via fingerprint, facial recognition, or PIN.
In Brief (TL;DR)
The fear that someone can steal money by bringing a POS close to your card is widespread, but it is an extremely rare event thanks to multiple and robust security measures.
In reality, contactless technologies and banking regulations offer several levels of protection that make this scenario an extremely rare occurrence.
Let’s discover together why, despite widespread fears, technological barriers and the traceability of every transaction make this specific theft scenario a very rare and difficult event to achieve.
Conclusions

In conclusion, the fear that someone could steal our money simply by bringing a POS close to our contactless card, however understandable, clashes with a solid reality made of technological and procedural barriers. The combination of the short range of NFC technology, spending limits, anti-fraud controls, encryption, and tokenization makes this type of theft a difficult, risky, and above all unprofitable enterprise for any malicious person. The intrinsic traceability of every transaction made via a legal POS represents the definitive deterrent, exposing the criminal to almost certain identification.
The real threats in the world of digital payments lie elsewhere, mainly in online scams like phishing, which exploit human naivety rather than technology vulnerabilities. Adopting simple but effective habits, such as activating notifications and periodically checking your statement, is more than enough to sleep soundly. Contactless technology is safe and represents a perfect example of how innovation can simplify our daily lives without compromising the protection of our assets. We can therefore continue to use our cards with confidence, enjoying the speed and convenience they offer.
Frequently Asked Questions

Technically it is possible, but it is an extremely rare and complex event. A malicious person would need to have an active POS, linked to a traceable bank account, and bring it within a few inches of your card to initiate the transaction. Obstacles such as the thickness of the wallet, the presence of multiple cards, or protective cases make the operation even more difficult.
In Italy and much of Europe, the limit for a single contactless transaction without entering the PIN code is set at 50 euros. For higher amounts, PIN authentication is always required, effectively blocking larger withdrawals. Furthermore, banks set cumulative limits: after a certain number of payments or once a total threshold (e.g., 150 euros) is reached, the PIN is required even for small sums as a security measure.
Simple and effective solutions exist. You can use wallets or cases with RFID shielding, which block radio waves preventing communication between the card and a POS reader. Even keeping multiple contactless cards overlapping in the same slot can create interference and prevent correct reading. An excellent habit is to activate notifications via app or SMS for every transaction and periodically check your account statement.
Yes, products with RFID (Radio Frequency Identification) shielding are effective. They work by creating a barrier with specific materials, usually metallic, that prevent the card’s NFC chip from being read by unauthorized external devices. Purchasing a shielded wallet or case is a valid and recommended preventive measure to increase the security of your cards.
If you notice a suspicious transaction, the first thing to do is immediately contact your bank to block the card and prevent further charges. Subsequently, dispute the operation and file a report with law enforcement. According to regulations, for unauthorized operations, the bank is required to refund the amount, unless it demonstrates gross negligence on the part of the customer.
Still have doubts about POS Theft: Are They Stealing Money From Your Card? The Truth?
Type your specific question here to instantly find the official reply from Google.








Did you find this article helpful? Is there another topic you’d like to see me cover?
Write it in the comments below! I take inspiration directly from your suggestions.